Our development teams continue to improve Progress Flowmon. The latest update takes the core Flowmon product to version 12.4, and our Anomaly Detection System (ADS) becomes release 12.4.
For Flowmon 12.4, we want to highlight its newest capability: IP Indexing.
Faster Searches with IP Indexing
Users can reduce the time required to process a query using the Analysis feature in Flowmon Monitoring Center. The performance improvement can be significant when using IP addresses as filtering parameters. A typical use case is a retrospective analysis of compromise indicators. For example, a user can receive a near-immediate answer to the question, “Did anyone from my network communicate with the following malicious IPs last month?” The performance improvement of a particular data query will always depend on a specific data set for a given period of time.
How To Enable IP Indexing?
You don’t need to do anything. IP indexing is enabled by default after upgrading to Flowmon 12.4. You can control the IP Indexing feature via Configuration Center → FMC Configuration → Basic Settings. IP Indexing is not applied retroactively. The IP Index is being generated for all incoming network telemetry data since the feature is enabled. Keep in mind that the subject of indexing are IP addresses in all channels of the “All sources” profile. Rebuilding an index for historical data is possible through a remote session with our support team.
There is a dedicated blog post covering IP Indexing in more depth, and the video demonstrates the significant speed improvements when using IP Indexed queries.
Usability improvements
Enhancements to productivity that will streamline workflows are available via Monitoring Center → Analysis. Some notable improvements are:
- IP Conversation is now a default option for TOP statistics in the Analysis
- In the Analysis chart, it is now possible to enable/disable NPM metrics individually
IP Address Metadata in Monitoring Center and Dashboards and Reports
IP addresses in query results on the Analysis page, and in Dashboards and Reports, now have an additional application information icon providing immediate insight into the application or platform behind an external IP address. Additionally, IP addresses with poor reputation (in Flowmon ADS so called Blacklists) are also highlighted with an icon for easy identification. This new feature is available only when ADS 12.4 is installed.
What's New in Flowmon ADS 12.4
The improvements in Flowmon ADS 12.4 build upon the updates in ADS 12.3. Details are available in this previous blog.
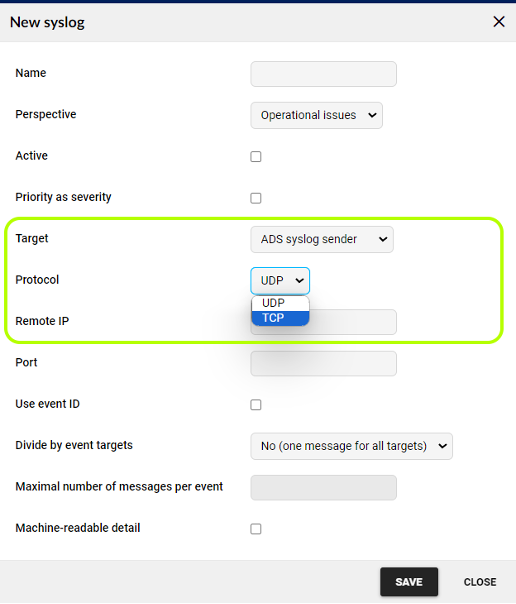
Event Reporting with Syslog Messages Using the TCP Protocol
Previously, only the UDP protocol could be used for a direct target, or TCP for all targets defined in the Configuration Center.
With the new release, the event reporting using Syslog is now more flexible. Events enable reporting to a specific target (IP:port) using the TCP protocol.
To use this feature, go to the Settings → Processing → Custom Actions → Syslog message and when creating or editing a Syslog, use “ADS syslog sender” as the target, and then select the TCP protocol as shown in the following picture.
Additional Improvements Include:
- Increased load speed of the Analysis page and its content in event-heavy deployments.
- Analysis Summary is loaded in parallel to the rest of the content on the Analysis page.
- Data Feeds page response improved when making actions (edit, delete, start, stop) on installations with many Data Feeds.
Find Out More
Visit the Flowmon platform page for details of Flowmon solution and the Flowmon ADS page for further information on network detection and response capabilities. Contact us and start a conversation with an expert about how Flowmon can help improve the security of your networks.
For a free trial of Flowmon to see how it can deliver actionable insights for your organization in minutes, visit our free trial page. Our team will assist you during your free trial testing. Use the contact page to start a conversation with our Flowmon team.
Filip Cerny
View all posts from Filip Cerny on the Progress blog. Connect with us about all things application development and deployment, data integration and digital business.
Comments
Topics
Sitefinity Training and Certification Now Available.
Let our experts teach you how to use Sitefinity's best-in-class features to deliver compelling digital experiences.
Learn MoreMore From Progress
Latest Stories
in Your Inbox
Subscribe to get all the news, info and tutorials you need to build better business apps and sites