Checkmarx One
Malicious Package Protection
Identify – and eliminate the dangers of – malicious and suspicious open source packages throughout the software development lifecycle (SDLC).

Reduce the Risks of Malicious Packages
Leverage Checkmarx’ automated scanning technologies and massive proprietary database of malicious packages to identify and remediate dangerous open source code in your applications.
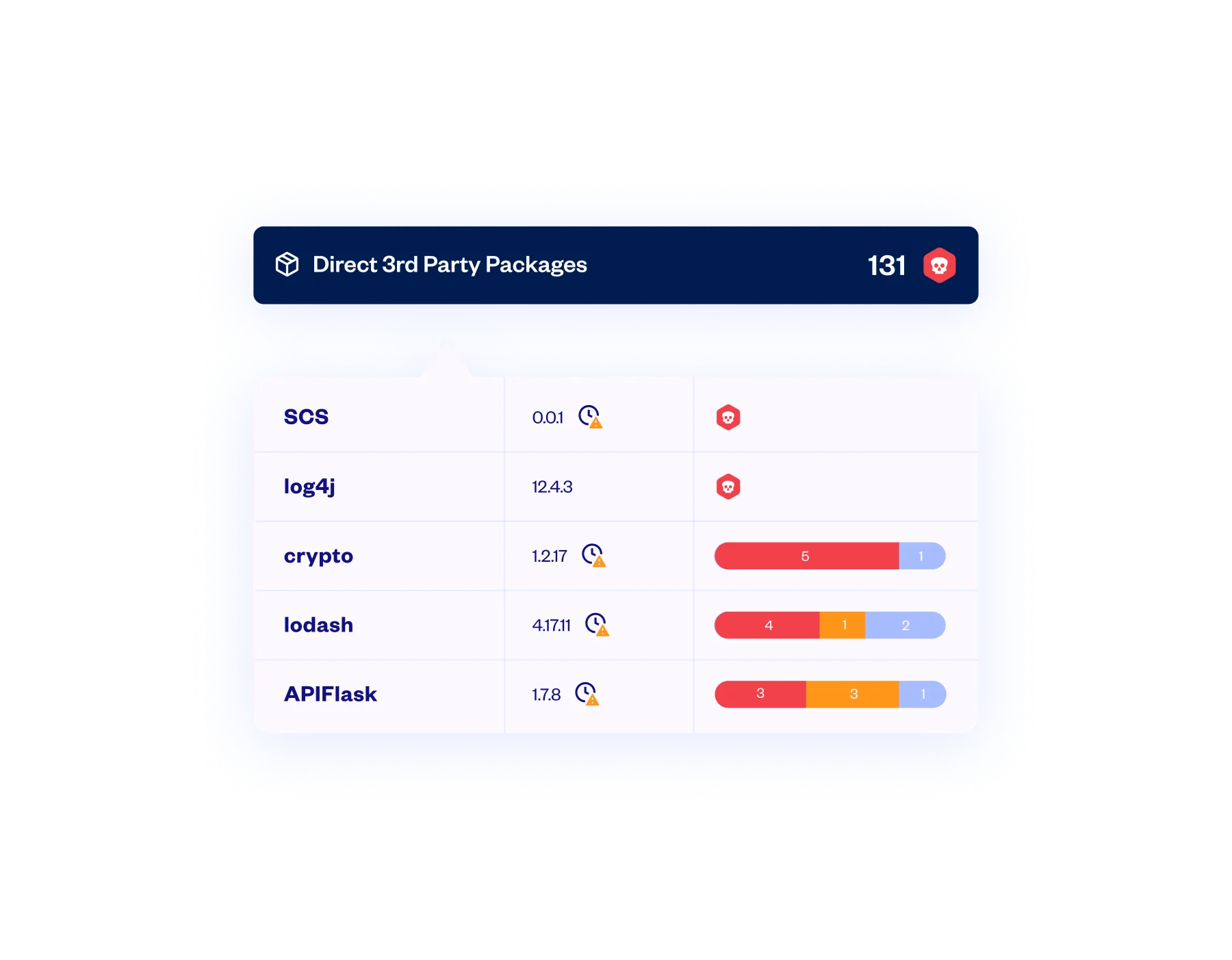
Deep Malicious Package Detection
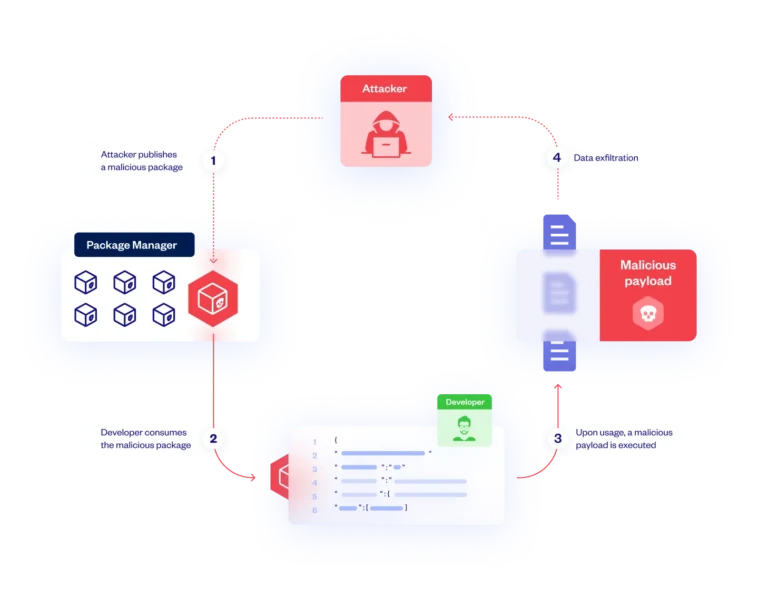
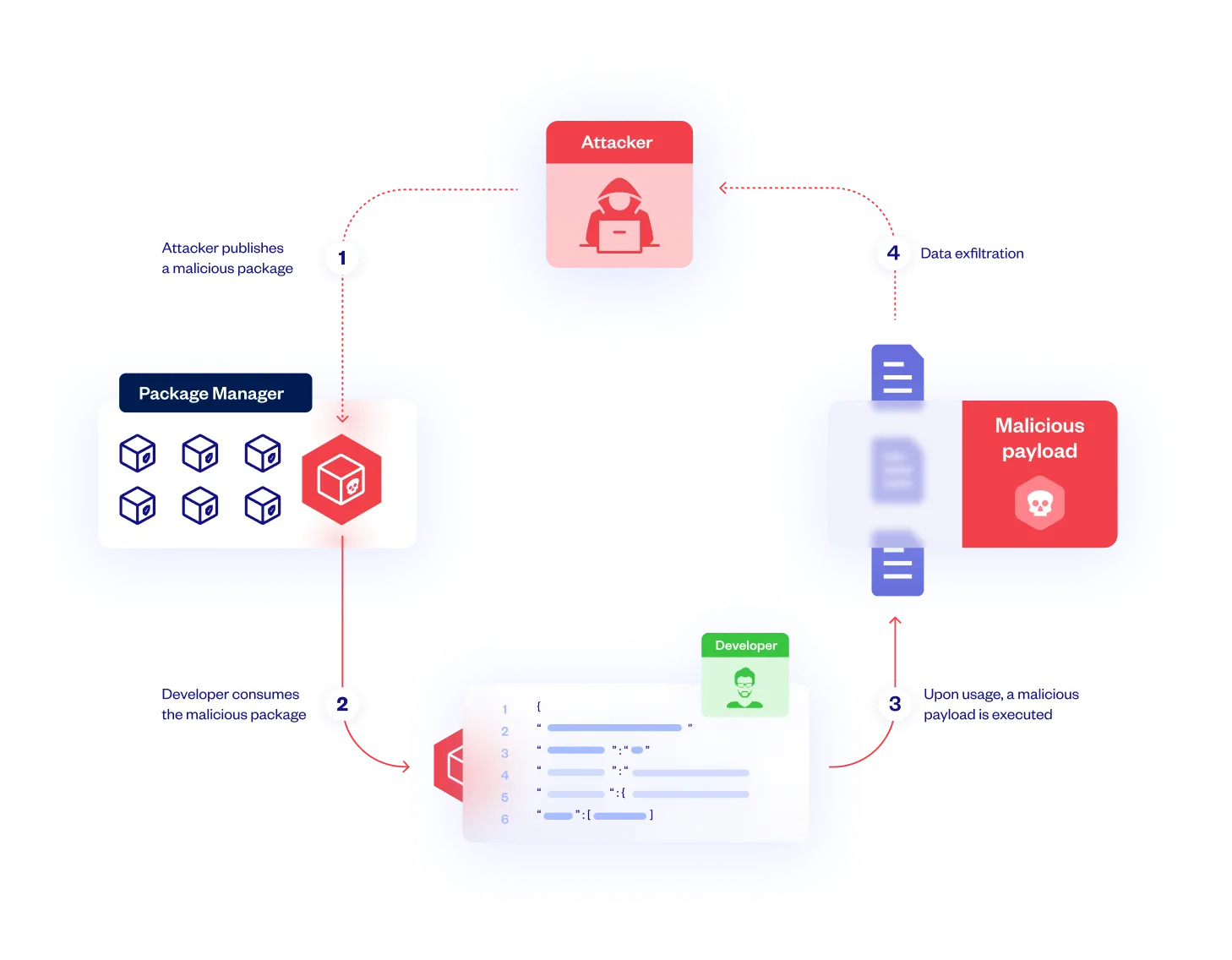
Checkmarx detects all open source packages in use, including dependencies of other packages, to identify those known to contain malware or exhibit suspicious behavior.
Unparalleled Malicious Packages Database

Checkmarx’ multi-layered package analysis methodologies have identified more than 400,000 malicious packages to date.
From Pre-Production to Runtime

Checkmarx detects malicious packages in manifest files, binaries, and containers – and correlates runtime usage data available from Sysdig to prioritize remediation efforts.
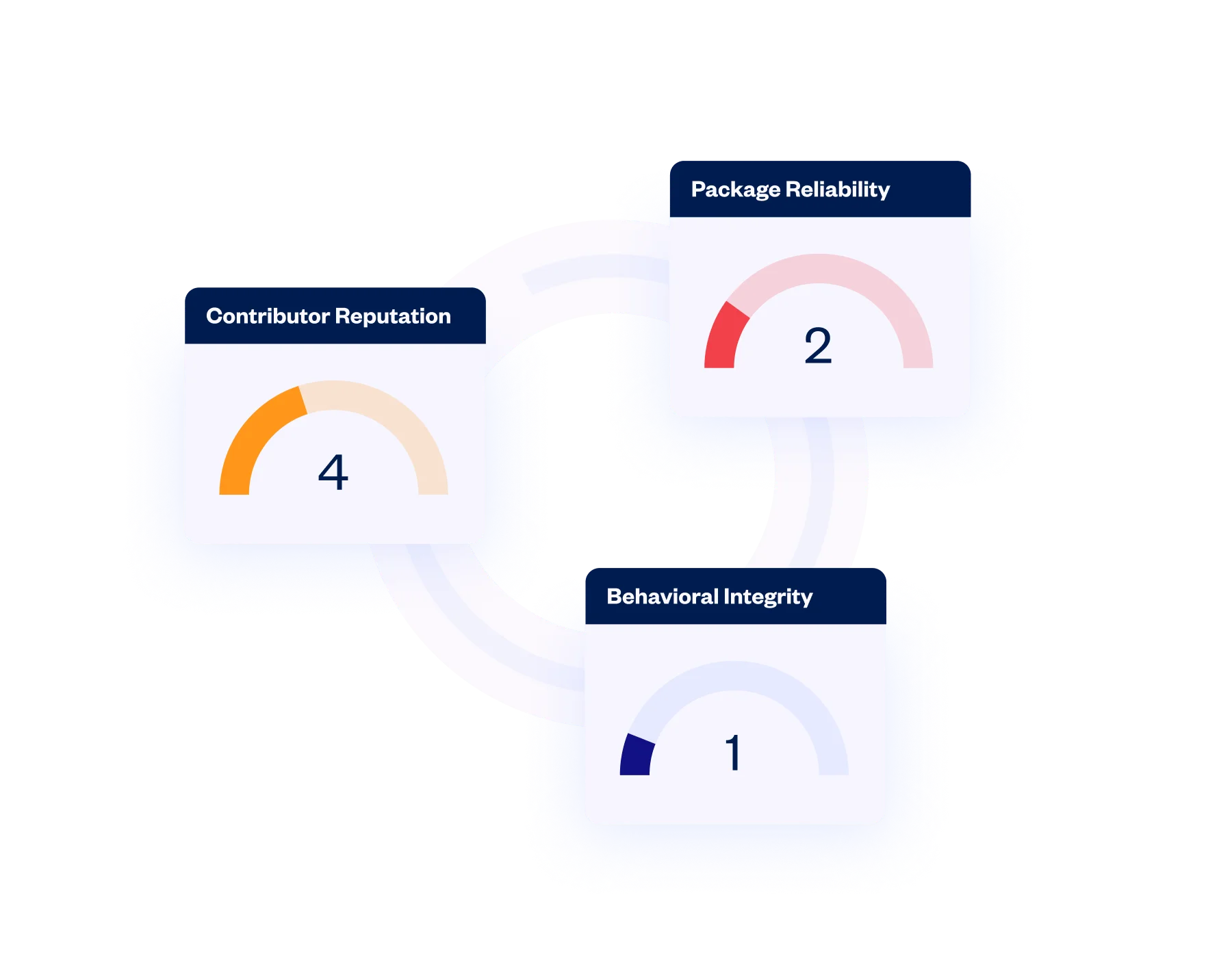
Package Reliability Metrics
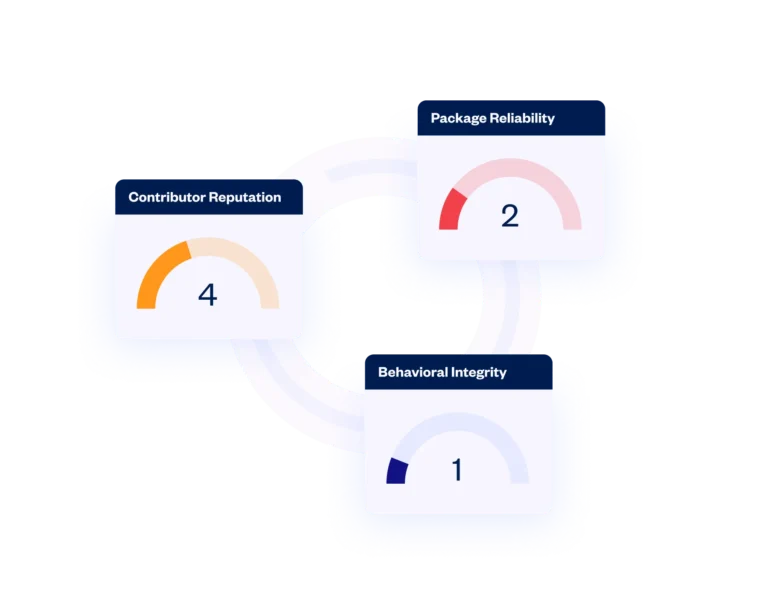
Checkmarx rates the trustworthiness of each open source package included in your applications, by package legitimacy, behavioral integrity and contributor reputation.
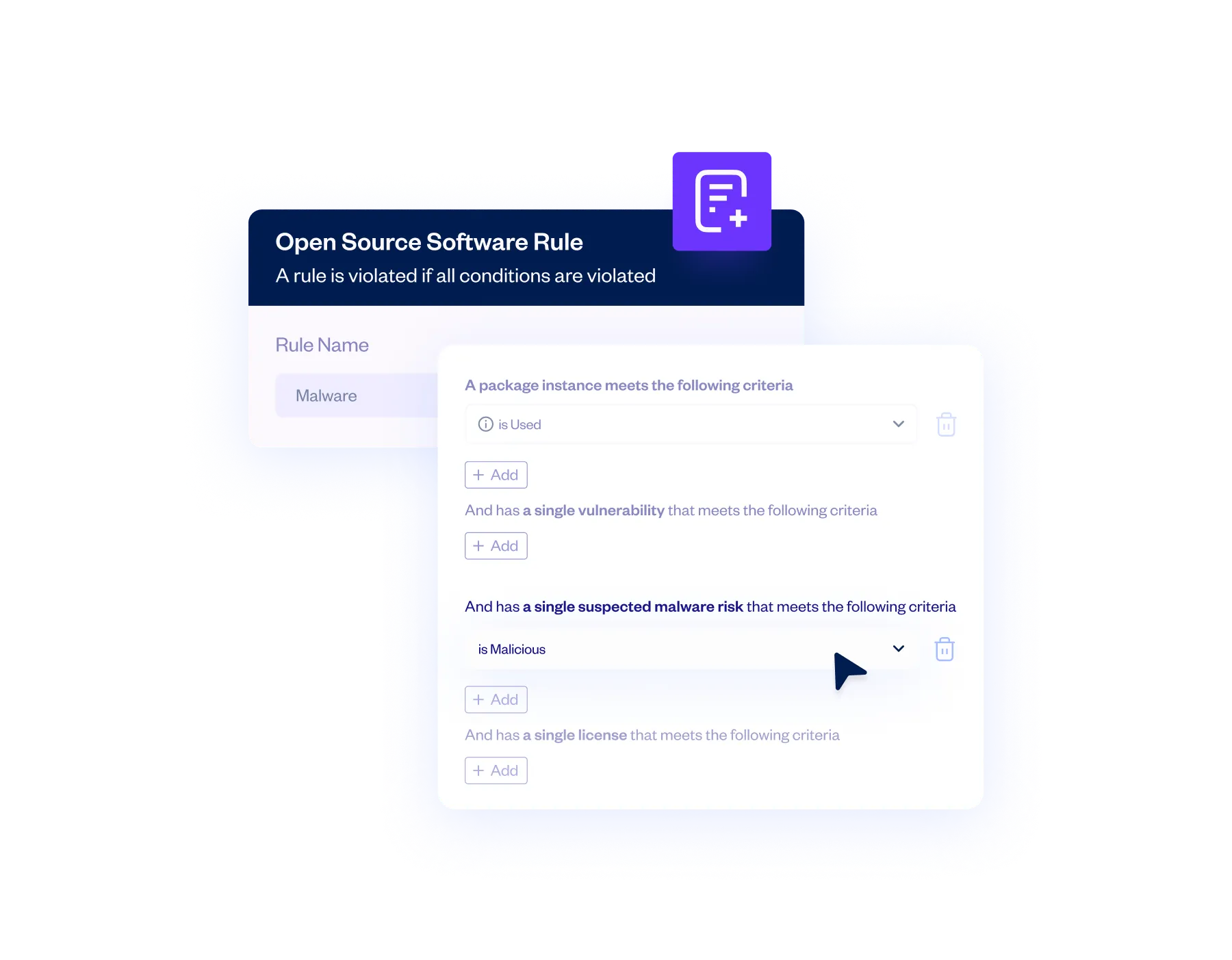
Automated Policy Actions
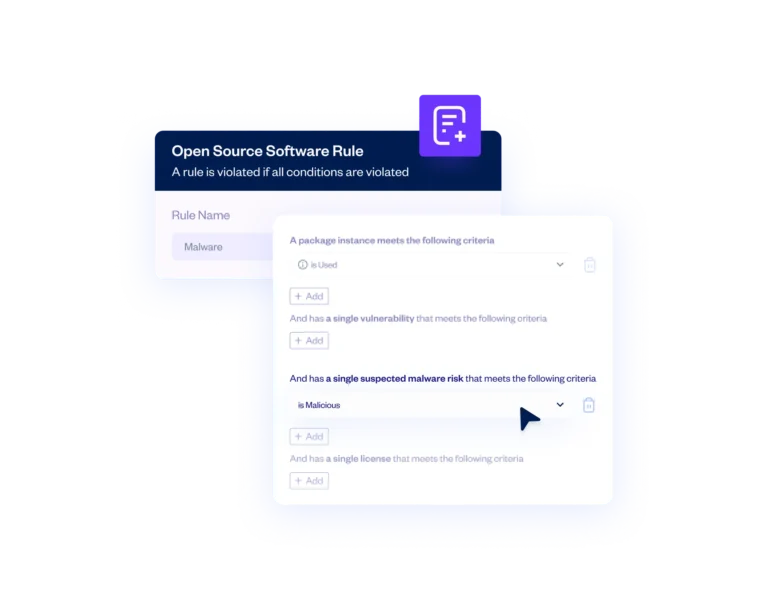
Defined policies automatically take effect when malicious packages are detected. This can include sending alerts, generating incident reports, preventing pull requests and breaking builds.
-
Deep Malicious Package Detection
Checkmarx detects all open source packages in use, including dependencies of other packages, to identify those known to contain malware or exhibit suspicious behavior.
-
Unparalleled Malicious Packages Database
Checkmarx’ multi-layered package analysis methodologies have identified more than 400,000 malicious packages to date.
-
From Pre-Production to Runtime
Checkmarx detects malicious packages in manifest files, binaries, and containers – and correlates runtime usage data available from Sysdig to prioritize remediation efforts.
-
Package Reliability Metrics
Checkmarx rates the trustworthiness of each open source package included in your applications, by package legitimacy, behavioral integrity and contributor reputation.
-
Automated Policy Actions
Defined policies automatically take effect when malicious packages are detected. This can include sending alerts, generating incident reports, preventing pull requests and breaking builds.


Trust Checkmarx for Your Code-to-Cloud Application Security
Learn how leading enterprises use Checkmarx to eliminate the threats of malicious packages and other open source software (OSS) dangers.
What’s in it for you
Protect your Organization from the Dangers of Malicious Packages
Reduce OSS security threats and improve your overall security posture by ensuring that no malicious or suspicious third-party packages are putting your organization at risk.
FAQ
What are malicious packages?
A malicious package is a piece of code disguised as a legitimate software component but designed to harm systems or steal data. Unlike packages that only contain unintentional security weaknesses (vulnerabilities) that can potentially be exploited by bad actors, malicious packages are designed and propagated with malevolent intent.
How prevalent are malicious packages?
The threat level to organizations of supply chain attacks in general, and malicious packages in particular, has been rapidly rising over the past few years. The numbers tell a disturbing story: Checkmarx’ AppSec research team has discovered more than 385,000 publicly available malicious packages (as of July 2024). 76% of CISOs are concerned about the dangers of malicious packages (Checkmarx survey, 2024). The average cost of a software supply chain compromise was $4.63 million, which is 8.3% higher than the average cost of a data breach due to other causes (IBM, 2023). It is imperative that CISOs and AppSec teams place more focus on this critical threat vector.
How does Checkmarx identify malicious packages?
Checkmarx combines proprietary technology with a team of expert security researchers to effectively identify malicious packages. Our threat intelligence system performs automated tests to identify suspicious package behaviors, author reputation, and additional checks (secrets, code scanning, static analysis, etc.). When a package is flagged as potentially malicious, our security research team conducts a thorough manual review to confirm its malicious nature, and avoid false positives, before adding it to our database (and reporting it externally, when appropriate). On average, Checkmarx scans nearly 2 million OSS packages every month.
What are examples of malicious and suspicious package behaviors?
A few examples include data exfiltration (stealing sensitive information), harmful file download, network connection to domain address known to be used by attackers, crypto-mining software, repojacking (takes control of the repository of a legitimate package), typosquatting (mimics the name of a popular package, inducing users to inadvertently use this package), chainjacking (stores a package in a renamed GitHub repository), and protestware (software that includes functionality which aims to protest an issue).
How can I protect myself from malicious packages?
The most effective way to prevent harm to your organization from malicious packages is to validate each package before it is installed. Beyond this, it is important to frequently scan all the OSS packages used in your applications and container images, to identify and remove/update any package versions that may have been flagged as containing malicious or suspicious code (note that most SCA solutions check for packages with vulnerabilities, but do not identify malicious packages). Other best practices include only using trusted repositories, only using OSS from reputable authors/maintainers, and keeping packages updated to the latest versions (so that you are benefiting from the most recent security patches). Learn more about Checkmarx’ SCA scan technology.
Where do most malicious packages come from?
Bad actors tend to focus on widely used packages and widely used repositories. Prominent examples include distributing JavaScript npm malicious packages via the npm Registry, Python malicious packages via the Python Package Index (PyPI), .NET NuGet malicious packages via the NuGet Gallery, and all types of malicious software packages via GitHub Packages.
Checkmarx One
The Cloud-Native Enterprise Application Security Platform
Checkmarx One delivers a full suite of enterprise AppSec solutions in a unified, cloud-based platform that allows enterprises to secure their applications from the first line of code to deployment in the cloud. Get everything your enterprise needs to integrate AppSec across every stage of the SDLC and build a successful AppSec program.
Application Security Posture
Management (ASPM) Consolidated, correlated, prioritized insights to help your team manage risk
Code
AI Powered-
Conduct fast and accurate scans to identify risk in your custom code.
-
Identify vulnerabilities only seen in production and assess their behavior.
-
Eliminate shadow and zombie APls and mitigate API-specific risks.
Supply Chain
AI Powered-
Easily identify, prioritize, remediate, and manage open source security and license risks.
-
Detect and remediate malicious or suspicious third-party packages that may be endangering your organization.
-
Built to accelerate AppSec teams and help developers secure applications from the first line of code.
-
Minimize risk by quickly identifying and eliminating exposed secrets.
-
Reduce security risks by health-scoring the code repositories used in your applications.
Cloud
AI Powered-
Scan container images, configurations, and identify open source packages and vulnerabilities preproduction and runtime.
-
Automatically scan your laC files for security vulnerabilities, compliance issues, and infrastructure misconfigurations.
Dev Enablement
-
Secure code training to upskill your developers and reduce risk from the first line of code.
Services
-
Maximize ROI with prioritized technical support, metrics monitoring, and operational assistance.
-
Augment your security team with Checkmarx services to ensure the success of your AppSec program.
-
Assess the current state of your AppSec program, benchmark against peers, and get actionable next steps for improvement.
Unified Dashboard, Reporting & Risk Management
Application Security Posture
Management (ASPM)
Consolidated, correlated, prioritized insights to help your team manage risk
AI Powered
Code
-
SAST
Static Application Security Testing (SAST)
Conduct fast and accurate scans to identify risk in your custom code.
-
DAST
Dynamic Application Security Testing (DAST)
Identify vulnerabilities only seen in production and assess their behavior.
-
API Security
API Security
Eliminate shadow and zombie APls and mitigate API-specific risks.
Supply Chain
-
SCA
Software Composition Analysis (SCA)
Easily identify, prioritize, remediate, and manage open source security and license risks.
-
Malicious Package Protection
Malicious Package Protection
Detect and remediate malicious or suspicious third-party packages that may be endangering your organization.
-
AI Security
AI Security
Built to accelerate AppSec teams and help developers secure applications from the first line of code.
-
Secrets Detection
Secrets Detection
Minimize risk by quickly identifying and eliminating exposed secrets.
-
Repository Health
Repository Health
Reduce security risks by health-scoring the code repositories used in your applications.
Cloud
-
Container Security
Container Security
Scan container images, configurations, and identify open source packages and vulnerabilities preproduction and runtime.
-
IaC Security
IaC Security
Automatically scan your laC files for security vulnerabilities, compliance issues, and infrastructure misconfigurations.
Get a Demo
Discover Checkmarx’ Malicious Package Protection
See how easy it is to ensure that malicious and suspicious OSS packages do not put your business at risk.
Trusted By: