The White House announced the launch of the US Cyber Trust Mark which aims to help buyers make an informed choice about the purchase of wireless internet-connected devices, such as baby monitors, doorbells, thermostats, and more.
The cybersecurity labeling program for wireless consumer Internet of Things (IoT) products is voluntary but the participants include several major manufacturers, retailers, and trade associations for popular electronics, appliances, and consumer products. The companies and groups said they are committed to increase cybersecurity for the products they sell.
Justin Brookman, director of technology policy at the consumer watchdog organization Consumer Reports, lauded the government effort and the companies that have already pledged their participation.
“Consumer Reports is eager to see this program deliver a meaningful U.S. Cyber Trust Mark that lets consumers know their connected devices meet fundamental cybersecurity standards,” Brookman said in a news release. “The mark will also inform consumers whether or not a company plans to stand behind the product with software updates and for how long.”
The Federal Communications Commission (FCC) proposed and created the labelling program and hopes it will raise the bar for cybersecurity across common devices, including smart refrigerators, smart microwaves, smart televisions, smart climate control systems, smart fitness trackers, and more.
The idea is that the Cyber Trust Mark logo will be accompanied by a QR code that consumers can scan for easy-to-understand details about the security of the product, such as the support period for the product and whether software patches and security updates are automatic.
The program is challenging because of the wide variety of consumer IoT products on the market that communicate over wireless networks. These products are built on different technologies, each with their own security pitfalls, so it will be hard to compare them, but at least the consumer will be able to find some basic—but important—information.
Even though participation is voluntary, manufacturers will be incentivized to make their smart devices more secure to keep the business of consumers who will choose products that only have the Cyber Trust Mark.
As we explained recently, the “Internet of Things” is the now-accepted term to describe countless home products that connect to the internet so that they can be controlled and monitored from a mobile app or from a web browser on your computer. The benefits are obvious for shoppers. Thermostats can be turned off during vacation, home doorbells can be answered while at work, and gaming consoles can download videogames as children sleep.”
And in 2024 we saw several mishaps ranging from privacy risks to downright unacceptable abuse. So, if we can avoid these incidents from happening again, then it surely is worth the trouble.
The testing of whether a product deserves the Cyber Trust Mark will be done by accredited labs and against established cybersecurity criteria from the National Institute of Standards and Technology (NIST).
The Cyber Trust Mark has been under constructions for quite a while was approved in a bipartisan unanimous vote last March, but we can expect the first logos to show up this year. And Anne Neuberger, deputy national security adviser for cyber, revealed that there are plans to release another executive order saying that, beginning in 2027, the Federal government will only buy devices that have the Cyber Trust Mark label on them.
For now, the program does not apply to personal computers, smartphones, and routers.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>One of the first things everyone predicted when artificial intelligence (AI) became more commonplace was that it would assist cybercriminals in making their phishing campaigns more effective.
Now, researchers have conducted a scientific study into the effectiveness of AI supported spear phishing, and the results line up with everyone’s expectations: AI is making it easier to do crimes.
The study, titled Evaluating Large Language Models’ Capability to Launch Fully Automated Spear Phishing Campaigns: Validated on Human Subjects, evaluates the capability of large language models (LLMs) to conduct personalized phishing attacks and compares their performance with human experts and AI models from last year.
To this end the researchers developed and tested an AI-powered tool to automate spear phishing campaigns. They used AI agents based on GPT-4o and Claude 3.5 Sonnet to search the web for available information on a target and use this for highly personalized phishing messages.
With these tools, the researchers achieved a click-through rate (CTR) that marketing departments can only dream of, at 54%. The control group received arbitrary phishing emails and achieved a CTR of 12% (roughly 1 in 8 people clicked the link).
Another group was tested against an email generated by human experts which proved to be just as effective as the fully AI automated emails and got a 54% CTR. But the human experts did this at 30 times the cost of the AI automated tools.
The AI tools with human assistance outperformed the CTR of these groups by scoring 56% at 4 times the cost of the AI automated tools. This means that some (expert) human input can improve the CTR, but is it enough to invest the time? Cybercriminals are proverbially lazy, which means they often exhibit a preference for efficiency and minimal effort in their operations, so we don’t expect them to think the extra 2% to be worth the investment.
The research also showed a significant improvement of the deceptive capabilities of AI models compared to last year, where studies found that AI models needed human assistance to perform on par with human experts.
The key to the success of a phishing email is the level of personalization that can be achieved by the AI assisted method and the base for that personalization can be provided by an AI web-browsing agent that crawls publicly available information.

Based on information found online about the target, they are invited to participate in a project that aligns with their interest and presented with a link to a site where they can find more details.
The AI-gathered information was accurate and useful in 88% of cases and only produced inaccurate profiles for 4% of the participants.
Other bad news is that the researchers found that the guardrails which are supposed to stop AI models from assisting cybercriminals are not a noteworthy barrier for creating phishing mails with any of the tested models.
The good news is that LLMs are also getting better at recognizing phishing emails. Claude 3.5 Sonnet scored well above 90% with only a few false alarms and detected several emails that passed human detection. Although it struggles with some phishing emails that are clearly suspicious to most humans.
If you’re looking for some guidance how to recognize AI assisted phishing emails, we’d like you to read: How to recognize AI-generated phishing mails. But the best way is to always remember the general advice not to click on any links in unsolicited emails.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
]]>A US chain of dental offices known as Westend Dental LLC denied a 2020 ransomware attack and its associated data breach, instead telling their customers that data was lost due to an “accidentally formatted hard drive.”
Unfortunately for the organization, the truth was found out. Westend Dental agreed to settle several violations of the Health Insurance Portability and Accountability Act (HIPAA) in a penalty of $350,000.
In October 2020, Westend Dental was attacked by the Medusa Locker ransomware group. Medusa Locker is a type of ransomware that operates under a Ransomware-as-a-Service (RaaS) model, primarily targeting large enterprises in sectors such as healthcare and education. This ransomware is known for employing double extortion tactics, which means they encrypt victims’ data while also threatening to release sensitive information unless a ransom is paid.
Westend Dental decided not to submit the mandatory notification within 60 days, waiting until October 28, 2022—two years later—to submit a data breach notification form to the State of Indiana.
The Indiana Office of Inspector General (OIG) later uncovered evidence that Westend Dental had experienced a ransomware attack on or around October 20, 2020, involving state residents’ protected health information, but Westend Dental still denied there had been a data breach. The investigation was prompted by a consumer complaint from a Westend Dental patient regarding an unfulfilled request for dental records.
In January 2023 a witness confirmed there had been a data breach, which prompted the Indiana OIG to initiate a wider investigation to assess compliance with the HIPAA rules and state laws. This investigation revealed extensive HIPAA violations.
A selection of the other violations that were found during the investigation include:
- HIPAA policies and procedures were not given to or made readily available to employees.
- The company provided no HIPAA training for employees prior to November 2023.
- Nothing showed evidence that a HIPAA-compliant risk analysis had ever been conducted (lists of usernames and passwords in plain text on the compromised server).
- There were no password policies until at least January 2024 (the same username and password were used for all Westend Dental servers that contained protected health information).
- No physical safeguards were implemented to limit access to servers containing patient data. (Some servers were located, unprotected, in employee break rooms and bathrooms.)
Court documents also reveal that because Westend Dental did not conduct a forensic investigation, the exact number of people affected by the breach is unknown. We do know that Westend Dental served around 17,000 patients across all companies and practices at the time of the ransomware attack.
The attackers initially gained access to at least one server, but since there was no monitoring software in place, it is unknown how far the attackers were able to infiltrate other systems. And since the backups that were made by a third party turned out to be incomplete, they were also unable to inform affected patients.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>During the holiday period on Malwarebytes Labs we covered:
- A day in the life of a privacy pro, with Ron de Jesus (Lock and Code S05E26)
- Task scams surge by 400%, but what are they?
- 5 million payment card details stolen in painful reminder to monitor Christmas spending
- AI-generated malvertising “white pages” are fooling detection engines
- Pallet liquidation scams and how to recognize them
- TP-Link faces US national security probe, potential ban on devices
- “Fix It” social-engineering scheme impersonates several brands
- Our Santa wishlist: Stronger identity security for kids
- 2024 in AI: It’s changed the world, but it’s not all good
- Is nowhere safe from AI slop? (Lock and Code S05E27)
- Data breaches in 2024: Could it get any worse?
- Connected contraptions cause conniption for 2024
- “Can you try a game I made?” Fake game sites lead to information stealers
And on the ThreatDown blog we covered:
- Top 5 most dangerous software weaknesses in 2024
- Cleo, the next MOVEit and GoAnywhere?
- Sysrv cryptomining botnet is still alive (and kicking out the competition)
- Clipboard hijacker tries to install a Trojan
- What is session hijacking?
- Which ports to monitor for ransomware attacks
Stay safe!
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
]]>The background and the IOCs for this blog were gathered by an Expert helper on our forums and Malwarebytes researchers. Our thanks go out to them.
A new, malicious campaign is making the rounds online and it starts simple: Unwitting targets receive a direct message (DM) on a Discord server asking about their interest in beta testing a new videogame (targets can also receive a text message or an email). Often, the message comes from the “developer” themselves, as asking whether you can try a game that they personally made is a common method to lure victims.
If interested, the victim will receive a download link and a password for the archive containing the promised installer.
The archives are offered for download on various locations like Dropbox, Catbox, and often on the Discord content delivery network (CDN), by using compromised accounts which add extra credibility.
What the target will actually download and install is in reality an information stealing Trojan.
There are several variations going around. Some use NSIS installers, but we have also seen MSI installers. There are also various information stealers being spread through these channels like the Nova Stealer, Ageo Stealer, or the Hexon Stealer.
The Nova Stealer and the Ageo Stealer are a Malware-as-a-Service (MaaS) stealer where criminals rent out the malware and the infrastructure to other criminals. It specializes in stealing credentials stored in most browsers, session cookie theft for platforms like Discord and Steam, and information theft related to cryptocurrency wallets.
Part of the Nova Stealer’s infrastructure is a Discord webhook which allows the criminals to have the server send data to the client whenever a certain event occurs. So they don’t have to check regularly for information, they will be alerted as soon as it gets in.
The Hexon stealer is relatively new, but we know it is based on Stealit Stealer code and capable of exfiltrating Discord tokens, 2FA backup codes, browser cookies, autofill data, saved passwords, credit card details, and even cryptocurrency wallet information.
One of the main interests for the stealers seem to be Discord credentials which can be used to expand the network of compromised accounts. This also helps them because some of the stolen information includes friends accounts of the victims. By compromising an increasing number of Discord accounts, criminals can fool other Discord users into believing that their everyday friends and contacts are speaking with them, emotionally manipulating those users into falling for even more scams and malware campaigns.
But the end goal to this scam, and most others, is monetary gain. So keep an eye on your digital and flat currency if you’ve fallen for one of these scams.
How to recognize the fake game sites
There is one very active campaign that uses a standard template for the website. This makes it easier for the cybercriminals to change name and location, but also for us to recognize them.
The websites are hosted by various companies that are very unresponsive to take down requests and usually protected by Cloudflare which adds an extra layer of difficulty for researchers looking to get the sites taken down. At which point they will easily set up a new one.
Another campaign uses blogspot to host their malware. These sites on blogspot have a different, but also standard, design.

Other effective measures to stay safe from these threats include:
- Having an up-to-date and active anti-malware solution on your computer.
- Verifying invitations from “friends” through a different channel, such as texting them directly or contacting them on another social media platform. Remember, their current account may have been compromised.
- Remembering to not act upon unsolicited messages and emails, especially when they want you to download and install something.
IOCs
Download sites:
dualcorps[.]fr
leyamor[.]com
crystalsiege[.]com
crystalsiege[.]online
dungeonofdestiny[.]pages.dev
mazenugame[.]blogspot.com
mazenugames.[]blogspot.com
yemozagame[.]blogspot.com
domenubeta[.]blogspot.com
domenugame[.]blogspot.com
The known download sites will be blocked by Malwarebytes/ThreatDown products which will also detect the information stealers.
We don’t just report on threats – we help protect your social media
Cybersecurity risks should never spread beyond a headline. Protect your social media accounts by using Malwarebytes Identity Theft Protection.
]]>The holidays are upon us, which means now is the perfect time for gratitude, warmth, and—because modern society has thrust it upon us—gift buying.
It’s Bluey and dig kits and LEGOs for kids, Fortnite and AirPods and backpacks for tweens, and, for an adult you particularly love, it’s televisions, air fryers, e-readers, vacuums, dog-feeders, and more, which all seemingly require a mobile app to function.
“The Internet of Things” is the now-accepted term to describe countless home products that connect to the internet so that they can be controlled and monitored from a mobile app or from a web browser on your computer. The benefits are obvious for shoppers. Thermostats can be turned off during vacation, home doorbells can be answered while at work, and gaming consoles can download videogames as children sleep on Christmas Eve.
And while some of these internet-connected smart devices can sound a little dumb—cue the $400 “smart juicer” that a Bloomberg reporter outperformed with her bare hands—there are legitimate cybersecurity risks at hand. Capable of collecting data and connecting to the internet, smart devices can also fall victim to leaking that data to hackers online.
As we enter the new year, Malwarebytes Labs is looking back at some of the strangest, scariest, and most dumbfounding smart device stories this past year. Read on and enjoy.
The million-car track hack
The latest vehicles filling up the local car lot might not strike you as “smart devices,” but upon closer inspection, these cars, SUVs, trucks, and minivans absolutely are. Replete with cameras and sensors that can track location, speed, distance travelled, seatbelt use, and even a driver’s eye movements, modern vehicles are, as many have described them, “smartphones on wheels.”
For years, the cybersecurity of these particularly mobile mobiles (sorry) was passable.
When a group of security researchers hacked into a Jeep Cherokee’s steering and braking systems in 2014, they were building off earlier research that required the hacker’s laptop to be physically connected to the Jeep itself—a comforting reality when imagining shadowy cybercriminals wresting control from a driver while sat behind a computer console hundreds of miles away. And while the security researchers were able to eventually hack the Jeep Cherokee without a physical connection, the work involved was still robust.
But early this year, a separate group of security researchers revealed that they could remotely lock, unlock, start, turn off, and geolocate more than a million Kia vehicles by knowing nothing more than the vehicle’s license plate number. The researchers could also activate a vehicle’s horn, lights, and camera.
The vulnerability wasn’t in the vehicles themselves, but in Kia’s online infrastructure (Kia fixed the vulnerability before the researchers published their findings).
In short, the researchers posed as Kia dealers when using an online Kia web portal and, by entering the Vehicle Identification Number—which could be revealed separately through license plate numbers—they could assign certain features like remote start and geolocation to a new account, which the security researchers controlled.
While the vulnerability did not provide access to any of the vehicles’ steering systems or acceleration or braking, it still posed an enormous privacy and security risk, said researcher Sam Curry in speaking to the outlet Wired:
“If someone cut you off in traffic, you could scan their license plate and then know where they were whenever you wanted and break into their car. If we hadn’t brought this to Kia’s attention, anybody who could query someone’s license plate could essentially stalk them.”
Whispering sweet nothings into your air fryer
There’s a modern urban legend that our smartphones listen to our in-person conversations to deliver eerily relevant ads, and while there’s no proof this is true, there are certainly a few stories that raise nearby suspicions.
Take, for instance, the case of the nosy air fryers.
On November 5, a UK consumer rights group named “Which?” published research into several categories of smart devices—TVs, smart watches, etc.—and what they discovered about three models of air fryers surprised many.
In testing the Xiaomi Mi Smart Air Fryer, the Cosori CAF-LI401S, and the self-titled Aigostar, the researchers discovered that the associated air fryer mobile apps for Android requested a startling amount of information:
“[As] well as knowing customers’ precise location, all three products wanted permission to record audio on the user’s phone, for no specified reason.”
The connected app for the Xiaomi air fryer “connected to trackers from Facebook, Pangle (the ad network of TikTok for Business), and Chinese tech giant Tencent (depending on the location of the user).” When creating an account for the Aigostar air fryer, the connected app asked users to divulge their gender and date of birth, without stating why that was necessary. The request, however, could be declined. The Aigostar app, like the Xiaomi app, sent personal data to servers in China, but this data sharing practice was clarified in the companies’ privacy policies, the researchers wrote.
The companies in the report pushed back on the characterizations from Which?, with a Xiaomi representative clarifying that “the permission to record audio on Xiaomi Home app is not applicable to Xiaomi Smart Air Fryer which does not operate directly through voice commands and video chat.” A representative for Cosori expressed frustration that the researchers at Which? did not share “specific test reports” with the company, as well.
The truth, then, may be somewhere in the middle. The air fryer mobile apps in question may request more information than necessary to function, but that could also be because the apps are trying to service the needs of many different types of products all at once.
A toothbrush tall tale
Let’s play a game of telephone: A Swiss newspaper interviews a cybersecurity expert about a hypothetical cyberattack and, days later, dozens of news outlets report that hypothetical as the truth.
This story did happen, and it would be far more disturbing if it wasn’t also tinged with a hint of humor, and that’s because the tall-tale-turned-“truth” involved a massive cyberattack launched by… toothbrushes.
In February, a Swiss newspaper article included an anecdote about a “Distributed Denial-of-Service” attack, or DDoS attack. DDoS attacks involve sending loads of connection requests (like regular internet traffic) to a certain webpage as a way to briefly overwhelm that web page and take it down. But the interesting thing about DDoS attacks is that they don’t require a laptop or a smartphone to make those requests—all they need is a device that can connect to the internet.
In the Swiss newspaper’s account, those devices were 3 million toothbrushes. Translated from the article’s original language in German, it read:
“She’s at home in the bathroom, but she’s part of a large-scale cyberattack. The electric toothbrush is programmed with Java, and criminals have, unnoticed, installed malware on it—like on 3 million other toothbrushes. One command is enough and the remote-controlled toothbrushes simultaneously access the website of a Swiss company. The site collapses and is paralyzed for four hours. Millions of dollars in damage is caused.”
The article, which noted that the whole scenario could’ve been ripped out of “Hollywood,” contextualized why the attack was so scary: It “actually happened.”
But it most assuredly had not.
The article had no details about the attack, so there was no company named, no toothbrush model specified, and no response from any organization. But none of that mattered as countless news outlets aggregated the original article, because what did matter was the virality of the whole affair. There was a device that seemingly everyone agreed had no reason to connect to the internet, and—would you look at that—it led to major consequences.
In reality, the consequences were to the truth.
This holiday season, let’s do better than the silliest, most needless IoT devices, and let’s connect to what matters instead.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
]]>It may sound weird when I say that I would like to remember 2024 as the year of the biggest breaches. That’s mainly because that would mean we’ll never see another year like it.
To support this nomination, I will remind you of several high-profile breaches, some of a size almost beyond imagination, some that really left us worried because of the type of data that was stolen, and a few duds.
Huge increase in numbers
As we reported in July, the number of data breach victims went up 1,170% in Q2 2024, compared to Q2 2023 (from 81,958,874 victims to 1,041,312,601).
The huge increase is no big surprise if you look at the size of some of these breaches. Remember these headlines?
5. Dell notifies customers about data breach (49 million customers)
4. “Nearly all” AT&T customers had phone records stolen in new data breach disclosure (73 million people).
3. 100 million US citizens officially impacted by Change Healthcare data breach.
2. Ticketmaster confirms customer data breach (560 million customers).
1. Stolen data from scraping service National Public Data leaked online (somewhere between 2.9 billion people (unconfirmed) and 272 million unique social security numbers).
The reason why I counted down to the biggest one, is because the first 4 are household names and people will know whether they might be affected since they are customers of the company. But National Public Data is a company that most people had never heard of before they read about the data breach.
The data gathered by National Public Data was “scraped,” meaning it was pulled from various sources and then combined in a large database. This also made it hard to get an exact number of affected people. The initially reported 2.9 billion people seemed a stretch, so we looked into that, and the estimates from our researchers say that it contains 272 million unique social security numbers. That could mean that the majority of US citizens were affected, although numerous people confirmed that it also included information about deceased relatives.
Sensitive data
Some of the huge breaches we listed contained Social Security Numbers (SSNs) which are a challenging process to be changed, but other breaches revealed all kinds of sensitive information.
Financial information was leaked by MoneyGram. Slim CD, Evolve Bank, Truist Bank, Prudential, and American Express.
Medical information was leaked by the earlier mentioned Change Healthcare breach, but we saw several smaller incidents at providers in the healthcare industry like Australia’s leading medical imaging provider I-MED Radiology, US and UK based healthcare provider DocGo that offers mobile health services, ambulance services, and remote monitoring for patients, nonprofit, outpatient provider of treatment for Opioid Use Disorder (OUD) CODAC Behavioral Healthcare, and DNA testing companies.
Ransomware incidents are also a big source of data breaches. When victims refuse to pay, the ransomware groups publish stolen data, as we saw with pharmacy chain Rite Aid.
Other sensitive data might have surfaced in hacktivist breaches at the Heritage Foundation, The Real World, and the Internet Archive. And sometimes it may be hard to not feel a bit of schadenfreude, as in the breach of the userbase of mobile monitoring app mSpy.
Anticlimaxes
In a few cases, there was a lot to do about something that turned out not to be so bad after all.
In February, a cybercriminal offered a business contact information database containing 132.8 million records for sale. It turned out to be a two-year-old third-party database which showed around 122 million unique business email addresses. That would have made it into our top 5, but the information in the database ages rather quickly. As soon as you move to a new job, that email address gets decommissioned and becomes worthless to phishers and other cybercriminals.
In July, a user leaked a file containing 9,948,575,739 unique plaintext passwords. The list was referred to as RockYou2024 because of its filename, rockyou.txt. However, without the associated user names or email, the list would have been of limited use to cybercriminals. If you don’t reuse passwords and never use “simple” passwords, like single words, then this release should not concern you.
If you were in any way affected by a data breach, we encourage you to have a look at our guide: Involved in a data breach? Here’s what you need to know.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>This week on the Lock and Code podcast…
You can see it on X. You can see on Instagram. It’s flooding community pages on Facebook and filling up channels on YouTube. It’s called “AI slop” and it’s the fastest, laziest way to drive engagement.
Like “click bait” before it (“You won’t believe what happens next,” reads the trickster headline), AI slop can be understood as the latest online tactic in getting eyeballs, clicks, shares, comments, and views. With this go-around, however, the methodology is turbocharged with generative AI tools like ChatGPT, Midjourney, and MetaAI, which can all churn out endless waves of images and text with little restrictions.
To rack up millions of views, a “fall aesthetic” account on X might post an AI-generated image of a candle-lit café table overlooking a rainy, romantic street. Or, perhaps, to make a quick buck, an author might “write” and publish an entirely AI generated crockpot cookbook—they may even use AI to write the glowing reviews on Amazon. Or, to sway public opinion, a social media account may post an AI-generated image of a child stranded during a flood with the caption “Our government has failed us again.”
There is, currently, another key characteristic to AI slop online, and that is its low quality. The dreamy, Vaseline sheen produced by many AI image generators is easy (for most people) to spot, and common mistakes in small details abound: stoves have nine burners, curtains hang on nothing, and human hands sometimes come with extra fingers.
But little of that has mattered, as AI slop has continued to slosh about online.
There are AI-generated children’s books being advertised relentlessly on the Amazon Kindle store. There are unachievable AI-generated crochet designs flooding Reddit. There is an Instagram account described as “Austin’s #1 restaurant” that only posts AI-generated images of fanciful food, like Moo Deng croissants, and Pikachu ravioli, and Obi-Wan Canoli. There’s the entire phenomenon on Facebook that is now known only as “Shrimp Jesus.”
If none of this is making much sense, you’ve come to the right place.
Today, on the Lock and Code podcast with host David Ruiz, we’re speaking with Malwarebytes Labs Editor-in-Chief Anna Brading and ThreatDown Cybersecurity Evangelist Mark Stockley about AI slop—where it’s headed, what the consequences are, and whether anywhere is safe from its influence.
Tune in today to listen to the full conversation.
Show notes and credits:
Intro Music: “Spellbound” by Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 4.0 License
http://creativecommons.org/licenses/by/4.0/
Outro Music: “Good God” by Wowa (unminus.com)
Listen up—Malwarebytes doesn’t just talk cybersecurity, we provide it.
Protect yourself from online attacks that threaten your identity, your files, your system, and your financial well-being with our exclusive offer for Malwarebytes Premium for Lock and Code listeners.
]]>A popular saying is: “To err is human, but to really foul things up you need a computer.”
Even though the saying is older than you might think, it did not come about earlier than the concept of artificial intelligence (AI).
And as long as we have been waiting for AI technology to become commonplace, if AI has taught us one thing this year, then it’s that when humans and AI cooperate, amazing things can happen. But amazing is not always positive.
There have been some incidents in the past year that have made many people even more afraid of AI than they already were.
We started off 2024 with a warning from the British National Cyber Security Centre (NCSC) telling us it expects AI to heighten the global ransomware threat.
A lot of AI related stories this year dealt with social media and other public sources that were scraped to train an AI model.
For example, X was accused of unlawfully using the personal data of 60 million+ users to train its AI called Grok. Underlining that fear, we saw a hoax go viral on Instagram Stories that told people they could stop Meta from harvesting content by copying and pasting some text.
Facebook had to admit that it scrapes the public photos, posts and other data from the accounts of Australian adult users to train its AI models, which no doubt contributed to Australia’s ban on social media for children under the age of 16.
As with many developing technologies, sometimes the race to stay ahead is more important than security. This was best demonstrated when an AI companion site called Muah.ai got breached and details of all its users’ fantasies were stolen. The hacker described the platform as “a handful of open-source projects duct-taped together.”
We also saw an AI supply-chain breach when a chatbot provider exposed 346,000 customer files, including ID documents, resumes, and medical records.
And if the accidents didn’t scare people off, there were also some outright scams targeting people that were eager to use some of the popular applications of AI. A free AI editor lured victims into installing an information stealer which came in both Windows and MacOS flavors.
We saw further refinement of an ongoing type of AI-supported scam known as deepfakes. Deepfakes are AI-generated realistic media, created with the aim of tricking people into thinking the content of the video or image actually happened. Deepfakes can be used in scams and in disinformation campaigns.
A deepfake of Elon Musk was named the internet’s biggest scammer as it tricked an 82-year-old into paying $690,000 through a series of transactions. And AI-generated deepfakes of celebrities, including Taylor Swift, led to calls for laws to make the creation of such images illegal.
Video aside, we reported on scammers using AI to fake the voices of loved ones to tell them they’ve been in an accident. Reportedly, with the advancements in technology, only one or two minutes of audio—perhaps taken from social media or other online sources—are needed to generate a convincing deepfake recording.
Voice recognition doesn’t always work the other way around though. Some AI models have trouble understanding spoken words. McDonalds ended its AI drive through order taker experiment with IBM after too many incidents, including customers getting 260 Chicken McNuggets or bacon added to their ice cream.
To sign off on a positive note, a mobile network operator is using AI in the battle against phone scammers. AI Granny Daisy uses several AI models that work together listening to what scammers have to say, and then responding in a lifelike manner to give the scammers the idea they are working on an “easy” target. Playing on the scammers’ biases about older people, Daisy usually acts as a chatty granny while at the same time wasting the scammers’ time that they can’t use to work on real victims.
What do you think? Do the negatives outweigh the positives when it comes to AI, or is it the other way round? Let us know in the comments section.
]]>Sorry for the headline, but we have to get creative to get anyone to read an article on a Friday like this one, even if it is an important story.
As we enter the holidays and parents begin to rest after another hectic year of shopping for their kids, Malwarebytes Labs wants to draw some attention to a part of most children’s lives that deeply affects their online security: The education system.
Although children in the US can’t take out loans or get credit cards on their own, they can end up as victims of identity theft, which can end up being a lifelong burden in the form of bad credit ratings and even criminal records.
An old study by Experian estimated that 25 percent of children will be victims of identity fraud or theft by the time they are 18 years old. In the current system it’s even possible that a newborn gets assigned a Social Security Number (SSN) which has already been used by a criminal.
The Social Security Administration (SSA) has already assigned more than half of all available SSNs and because there is no check before the number gets issued, a baby could end up getting one with a bad history.
But usually, it happens later on. According to Javelin’s 2022 Child Identity Fraud Study, approximately 1.7 million US children had their personal information exposed and potentially compromised due to data breaches in 2021.
Many of the leaked information about children comes, unsurprisingly, from the educational institutions that they visit.
Breaches in education don’t follow a pattern or affect only children. They range from leaky school apps to ransomware and from childcare to the teacher’s retirement system.
Even though the Taxpayer First Act of 2019 mandates that the IRS notify taxpayers, including parents and guardians, when there is suspected identity theft, it has been criticized for not complying with this obligation.
So, parents and guardians need to be vigilant themselves.
How to keep an eye on your children’s identities
There are a few things you can do.
- Contact the three major credit bureaus (Equifax, Experian, and TransUnion) to check if your child has a credit report. Generally, children under 18 should not have a credit report. If a report exists, it may indicate identity theft. If a credit report is found, inform the credit bureau it may be fraudulent. You may need to provide documents to credit bureaus to verify your child’s identity and your own.
- If your child is under 16, you can request a free credit freeze to prevent new accounts from being opened in their name. This freeze remains in place until you request it to be removed. The process for getting a freeze for a minor is different than getting one for an adult. The credit bureaus give specific instructions at these three sites: Experian, Equifax, and TransUnion.
- Limit who you share your child’s Social Security number with and only provide it when absolutely necessary. Don’t be afraid to ask why the information is needed and how it will be protected.
- If you suspect your child’s identity has been stolen, report it to the Federal Trade Commission (FTC) at IdentityTheft.gov. Also, contact your local law enforcement to get a police report and notify the fraud departments of companies where fraudulent accounts were opened in your child’s name.
Check your digital footprint
If you want to find out what personal data of yours has been exposed online, you can use our free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and we’ll send you a free report.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>More and more, threat actors are leveraging the browser to deliver malware in ways that can evade detection from antivirus programs. Social engineering is a core part of these schemes and the tricks we see are sometimes very clever.
Case in point, there has been an increase in attacks that involve copying a malicious command into the clipboard, only to be later pasted and executed by the victims themselves. Who would have though that copy/paste could be so dangerous?
The new campaign we observed uses a a combination of malicious ads and decoy pages for software brands, followed by a fake Cloudflare notification that instructs users to manually run a few key combinations. Unbeknownst to them, they are actually executing PowerShell code that retrieves and installs malware.
The discovery
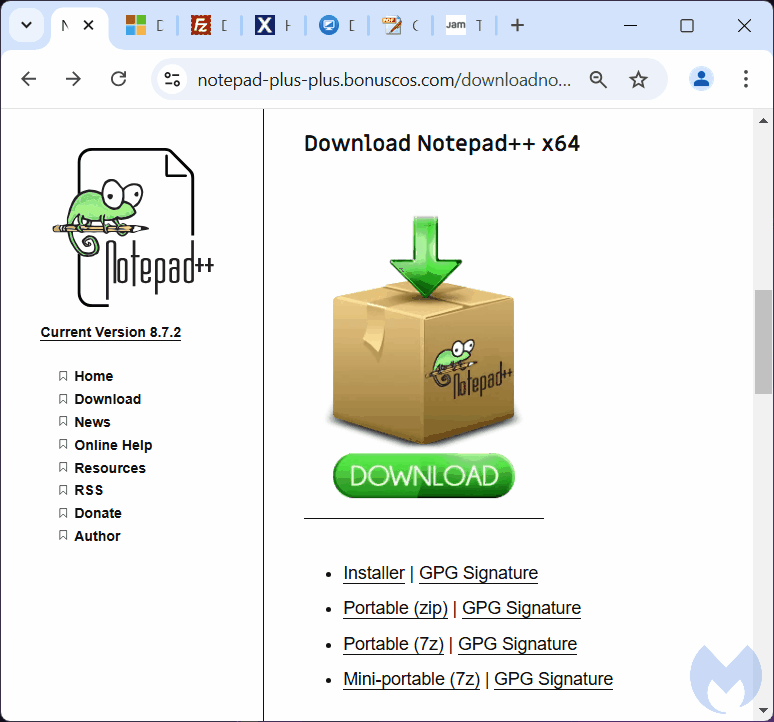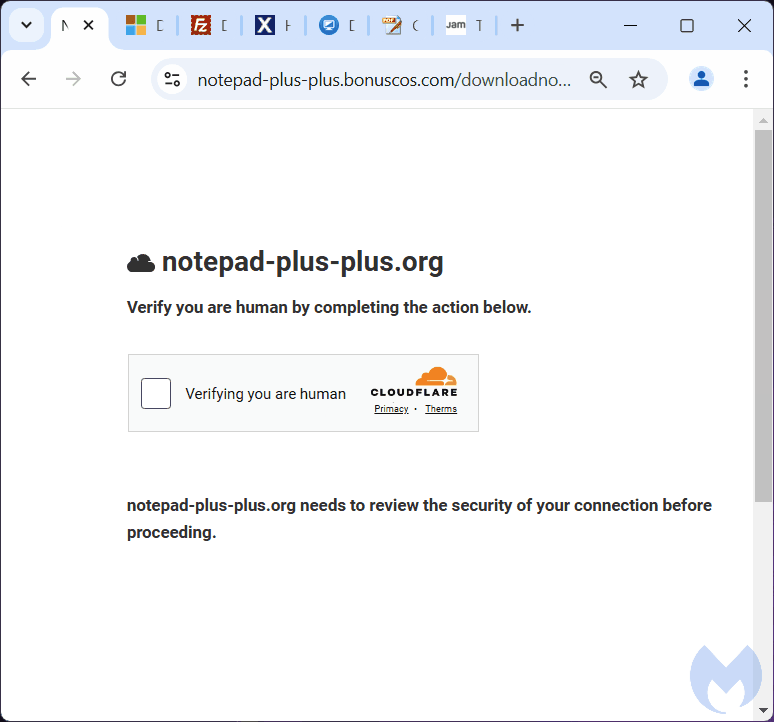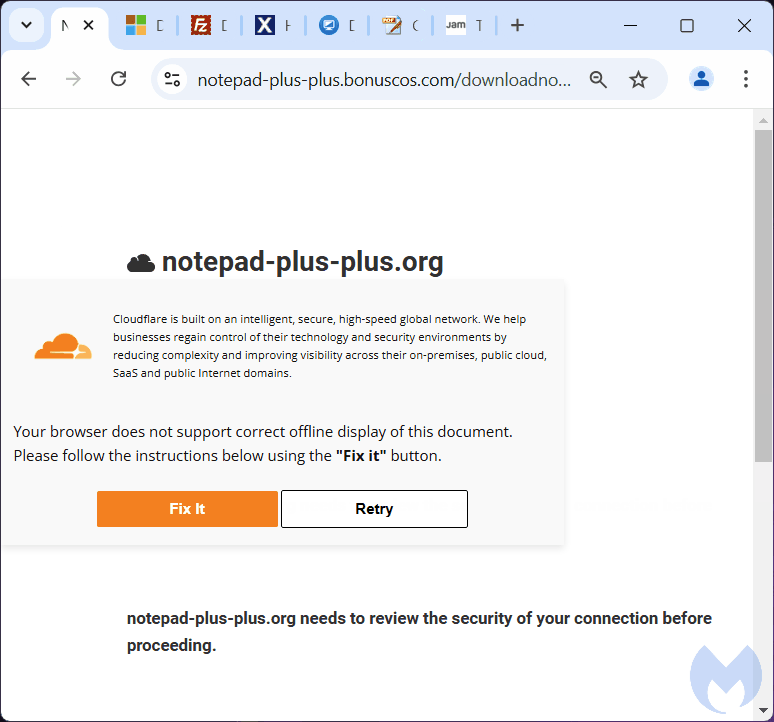
Our investigation into this campaign started from a suspicious ad for ‘notepad’ while performing a Google search. Such search queries have been a hot spot for criminals who want to lure victims that are looking to download programs onto their computer.

Based on previous evidence, criminals are tricking victims into visiting a lookalike site with the goal of downloading malware. In this case, the first part was true, but what unfolded next was new to us.
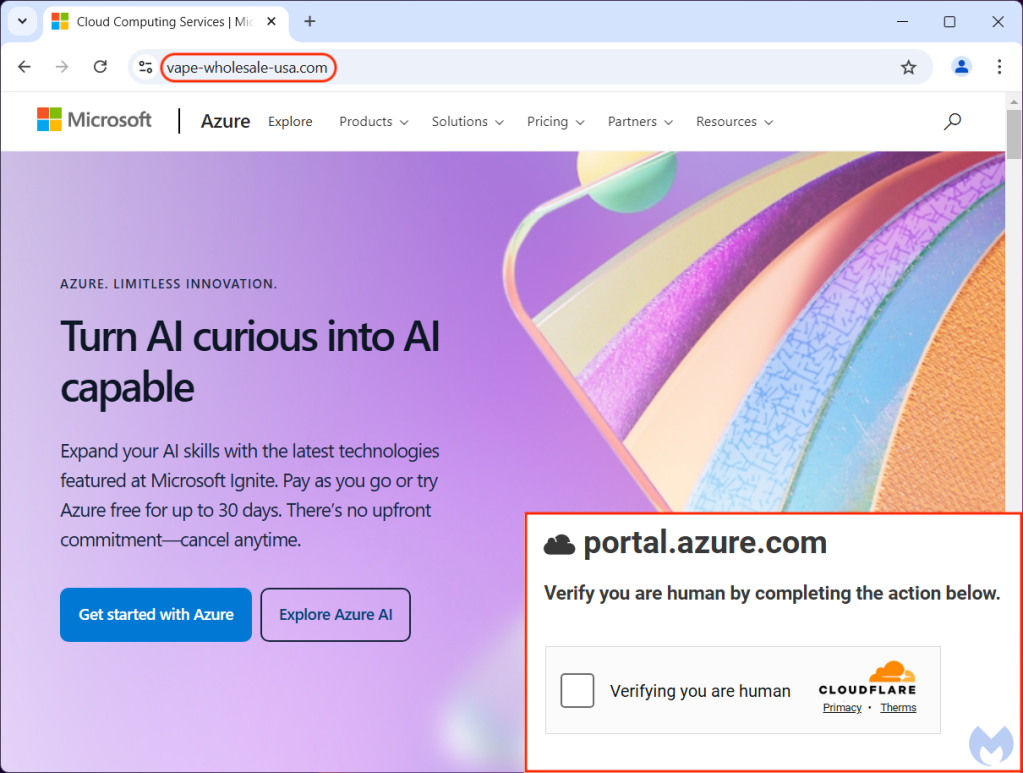
When we clicked the Download button, we were redirected to a new page that appeared to be Cloudflare asking us to “verify you are human by completing the action below“. This type of message is more and more common, as site owners try to prevent bots and other unwanted traffic.
But rather than having to solve a CAPTCHA, we saw another unexpected message: “Your browser does not support correct offline display of this document. Please follow the instructions below using the “Fix it” button“.
Powerful technique
This technique is actually not new in itself, and similar variants have been seen both via email spam and compromised websites before. It is sometimes referred to as ClearFake or ClickFix, and requires users to perform a manual action to execute a malicious PowerShell command.
Clicking on the ‘Fix It’ button copies that command into memory (the machine’s clipboard). Of course the user has no idea what it is, and may follow the instructions that ask to press the Windows and ‘R’ key to open the Run command dialog. CTRL+V pastes that command and Enter executes it.

Once the code runs, it will download a file from a remote domain (topsportracing[.]com) within the script. We tested that payload in a sandbox and observed immediate fingerprinting:
C:\Users\Admin\AppData\Local\Temp\10.exe
C:\Windows\SYSTEM32\systeminfo.exe
C:\Windows\system32\cmd.exe
C:\Windows\system32\cmd.exe /c "wmic computersystem get manufacturer"
The information is then sent back to a command and control server (peter-secrets-diana-yukon[.]trycloudflare[.]com) abusing Cloudflare tunnels:
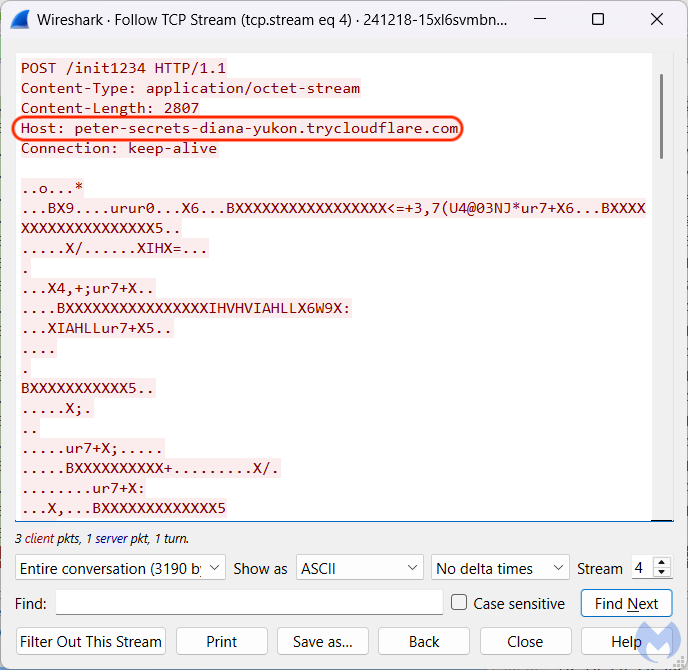
The use of Cloudflare tunnels by criminals was previously reported by Proofpoint to deliver RATs. We weren’t able to observe a final payload but it is likely of a similar kind, perhaps an infostealer.
Campaign targets several brands
This was not an isolated campaign for Notepad, as we soon found additional sites with a similar lure. There was a Microsoft Teams landing page which used exactly the same trick, followed by others such as FileZilla, UltraViewer, CutePDF and Advanced IP Scanner.





Oddly, we saw a lure for a cruise booking site. We have no idea how that came to be, unless the criminals agree that everyone needs a vacation sometimes.

Overlap with other campaigns
As mentioned previously, this type of social engineering attack is getting more and more popular. Researchers are tracking several different families under different names such as the original SocGholish.
Interestingly, the same domain (topsportracing[.]com) we saw in the malicious PowerShell command for Notepad++ was also used recently in another campaign known as #KongTuke:

As these schemes are being increasingly used by criminals, it is important to be aware of the processes involved. The Windows key and the letter ‘R’ pressed together open the Run dialog box. This is not something that most users will ever need to do, so always think carefully whenever you are instructed to perform this.
Malwarebytes customers are protected against this attack via our web protection engine for both the malicious sites and PowerShell command.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
Indicators of Compromise
Malicious domains
notepad-plus-plus.bonuscos[.]com
microsoft.team-chaats[.]com
cute-pdf[.]com
ultra-viewer[.]com
globalnetprotect[.]com
sunsetsailcruises[.]com
jam-softwere[.]com
advanceipscaner[.]com
filezila-project[.]com
vape-wholesale-usa[.]com
Servers used before Cloudflare proxy
185.106.94[.]190
89.31.143[.]90
94.156.177[.]6
141.8.192[.]93
Malware download URLs
hxxp[://]topsportracing[.]com/wpnot21
hxxp[://]topsportracing[.]com/wp-s2
hxxp[://]topsportracing[.]com/wp-s3
hxxp[://]topsportracing[.]com/wp-25
hxxp[://]chessive[.]com/10[.]exe
hxxp[://]212[.]34[.]130[.]110/1[.]e
Malware C2
peter-secrets-diana-yukon[.]trycloudflare[.]com]]>
The US government launched a national security investigation into the popular, Chinese-owned router maker TP-Link, with a potential eye on banning the company’s devices in the United States.
The investigation comes amid heightened tension between the US and the Chinese government, and after a public letter from members of the US House of Representatives this summer that alleged that TP-Link was engaged in predatory pricing practices, driven by ulterior motives, and possibly sponsored by China. US officials noted how TP-Link undercut the competition on price to become the market leader for Small Office/Home Office (SOHO) network appliances.
In doing this, TP-Link managed to grow their market share to 60% of the US retail market for WiFi systems and SOHO routers—from 10% in 2019. And the company reportedly has almost 80% of the US retail market for WiFi 7 mesh systems.
A WiFi 7 Mesh system is the latest advancement in wireless networking, combining the features of WiFi 7 technology with the benefits of mesh networking, which uses multiple nodes that work together to provide uniform WiFi coverage throughout the home, eliminating dead zones.
Because of TP-Link’s original founding in China, claims have been made of a so-called “Huawei playbook,” referring to allegations that Huawei Technologies Co. spies for the Chinese government and that it became a dominant player in the global networking equipment sector on the back of improper state subsidies. Huawei and China both deny these allegations, though.
Nonetheless, the US imposed restrictions that make it harder for Huawei to sell equipment in the US and buy parts from American suppliers.
Perhaps because of this type of scrutiny, TP-Link has made many efforts to distance itself from its Chinese ownership. TP-Link Systems is an entity based in Irvine, California, and no longer affiliated with the Chinese TP-Link Technologies.
Part of the attention paid to TP-Link this year could also be because a Chinese-backed Advanced Persistent Threat (APT) called Volt Typhoon has been using SOHO routers as gateways to get inside sensitive infrastructure. The cybercriminals used the routers to hide the actual origin of malicious attempts to reach inside the utilities and other targets.
But that argument doesn’t make sense since many of those routers were malware-infected NetGear and Cisco SOHO devices that no longer receive updates because they have reached their End-of-Life.
TP-Link said the market share percentages were overstated, but it did recently sign deals with internet service providers (ISPs) who then supply the routers to their customers. In such deals ISPs often rebrand the routers which makes it hard for customers to know which brand and type of router they have.
Representative John Moolenaar, the co-chairman of the US House Select Committee on Strategic Competition between the United States and the Chinese Communist Party—which sent the letter prompting the TP-Link probe—stayed fast in his concerns:
“Chinese companies that, because of the technology they provide or the supply chains they impact, pose an unacceptable risk to our country’s security.”
Unfortunately, vulnerabilities in routers are very common and hardly ever patched by consumers, because they either don’t know how, or they may not even know that the patches are necessary because they don’t know which router model they have or that patches are available.
This makes it very hard to tell whether a vulnerability was an oversight or an intentional backdoor. This will make it hard for the investigators to find the “loaded gun” they are looking for.
We don’t just report on privacy—we offer you the option to use it.
Privacy risks should never spread beyond a headline. Keep your online privacy yours by using Malwarebytes Privacy VPN.
]]>Pallet liquidation scams target people looking to purchase pallets of supposedly discounted merchandise, often from major retailers like Amazon.
Groups that engage in pallet liquidation sales are rampant on social media and it’s hard to discern the scammers from the legitimate ones (to be honest, I’ve always thought they were all scams, until someone told me there are legitimate ones), let alone the grey area in between.
The scams are based on the fact that many products are returned and can not be sold again for various reasons. But companies also offer overstock and out-of-season apparel for sale. Most of these companies have the first buyers sign non-disclosure agreements (NDAs) so when you scroll through different legitimate liquidation websites and marketplaces the origin of the pallet is almost never stated.
Depending on the reason of sale and the origin, the pallets may include a large quantity of one product or a mix of products, such as overstock or discontinued items, customer returns, or refurbished goods.
Given that the pallet liquidation market is a billion-dollar industry, it inevitably attracts scammers seeking to grab a piece of the action without putting in the work or risk.
In social media groups that specialize in pallet liquidation, you’ll find advertisements that promise valuable merchandise at significantly discounted prices, such as electronics, tools, or other high-demand items.

You’ll also see sponsored ads on social media about pallet sales (note: these are almost always fake).
The risk of not receiving what you have paid for is an obvious one, but some of these scammers will go the extra mile and set up fake websites where they will try and harvest payment details.
How to steer clear of pallet liquidation scams
If you’re really looking to try your luck at this, there are a few tips that can help you get your money’s worth.
The first thing to keep in mind is the higher up you are in the chain, the better your chances of making a profit are. It usually also means buying large quantities (I’m talking about truckloads) and larger investments. And most sellers do not have a return policy. I realize the large shipments are not for everyone, so here are some things to remember:
Red flags:
Unbelievable prices. The people you’re buying from are not stupid. If they are offering goods for unbelievable prices, don’t take their word for it.
Payment methods. Sellers who insist on payment methods that do not offer buyer protection are likely scammers.

Lack of manifest. Sellers that are unwilling to disclose any information about the content of a pallet shouldn’t be trusted. There is definitely a higher risk of damaged items.
Time pressure. Slogans like “Act now!” or “Only 3 left” are often used to create a false sense of urgency, hoping victims will purchase without applying the research below.
Research the seller:
Find contact information and check the validity. Legitimate liquidation sites provide clear and easily accessible contact details, including physical address, phone number, and email address. Be wary of sites that lack this information or provide vague or unreliable contact details.
Verify the physical address of the liquidation site through online maps or directories. A legitimate company is more likely to have a verifiable physical presence. After all, you can hardly receive these pallets in a PO box.
For a website you can use online tools to find the domain age and registration. Legitimate domains have a longer history so they are easier to research. New domains should be regarded as suspicious, since scammers have the habit of moving on to the next domain leaving bad reviews behind.
Check if the website is listed on the Better Business Bureau (BBB) website and review their rating and any associated complaints. It also allows you to check how long they’ve been in business.
Do an online search for the name of the company and combine it with terms like “scam” or “complaint” to help you find problems others may have run into in dealing with this company.
Don’t trust sponsored ads. We have heard of scammers that can afford to pay millions to advertise on Meta, Google, and other platforms and still make a handsome profit.
Use web protection like Malwarebytes Browser Guard. It flags malicious websites and credit card skimmers that steal your information.
Too late?
If you suspect that your payment card details have been stolen, these are the recommended actions:
- Regularly check account and card statements and notify your bank about any suspicious activity.
- Where possible, set up fraud alerts with your bank or payment card provider.
- Change the password and enable multi-factor authentication if you haven’t already.
- Freeze your credit so nobody can open any new accounts in your name.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>This is no secret, online criminals are leveraging artificial intelligence (AI) and large language models (LLMs) in their malicious schemes. While AI tends to be abused to trick people (i.e. deepfakes) in order to gain something, sometimes, it is meant to defeat computer security programs.
With AI, this process has just become easier and we are seeing more and more cases of fake content produced for deception purposes. In the criminal underground, web pages or sites that are meant to be decoys are sometimes called “white pages,” as opposed to the “black pages” (malicious landing pages).
In this blog post, we take a look at a couple of examples where threat actors are buying Google Search ads and using AI to create white pages. The content is unique and sometimes funny if you are a real human, but unfortunately a computer analyzing the code would likely give it a green check.
Fake-faced executives
The first example is a phishing campaign targeting Securitas OneID. The threat actors are very cautious about avoiding detection by running ads that most of the time redirect to a completely bogus page unrelated to what one would expect, namely a phishing portal.
It did cross our minds they could very well be trolling security researchers, but if that was truly the case, why not simply go for Rick Astley’s Never Gonna Give You Up?
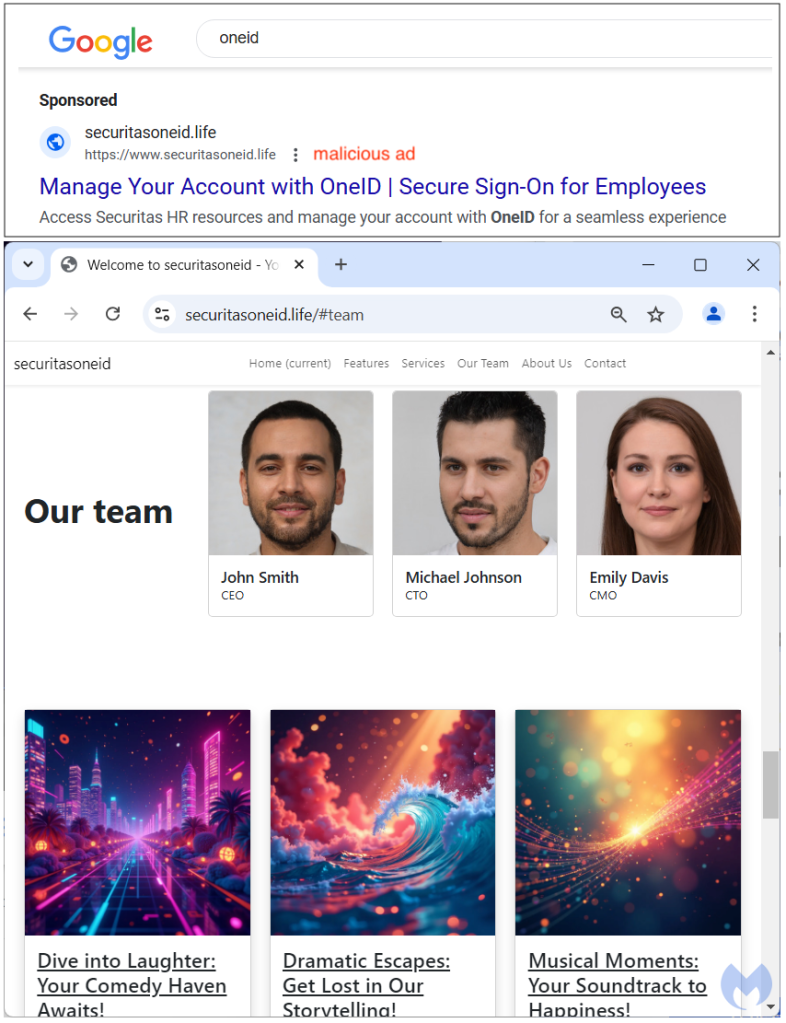
The entire site was created with AI, including the team’s faces. While in the past, criminals would go for stock photos or maybe steal a Facebook profile, now it’s easier and faster to make up your own, and it’s even copyright-free!

When Google tries to validate the ad, they will see this cloaked page with pretty unique content and there is absolutely nothing malicious with it.
Parsec and the universe
Our second example is another Google ad for Parsec this time, a popular remote desktop program used by gamers.
It so happens that a parsec is also an astronomical measurement unit and the threat actors (or should we say AI) went wild with it, creating a white page heavily influenced by Star Wars:

The artwork, including posters, is actually quite nice, even for a non-fan.

Once again, this cloaked content is a complete diversion which will take detection engines for a ride.
AI vs AI: humans to the rescue
These are just some of the many examples of AI being misused. In the early days of deepfakes, one may remember companies already training AI to detect AI.
There will naturally be content produced by AI for legitimate reasons. After all, nothing prohibits anyone from creating a website entirely with AI, simply because it’s a fun thing to do.
In the end, AI can be seen as a tool which on its own is neutral but can be placed in the wrong hands. Because it is so versatile and cheap, criminals have embraced it eagerly.
Ironically, it is quite straightforward for a real human to identify much of the cloaked content as just fake fluff. Sometimes, things just don’t add up and are simply comical. Do jokes trigger the same reaction in an AI engine as they would to a human? It doesn’t seem like it… yet.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
]]>Another day, another exposed S3 bucket.
This time, 5 million US credit cards and personal details were leaked online. The Leakd.com security team discovered that 5 terabytes of sensitive screenshots were exposed in a freely accessible Amazon S3 bucket.
An S3 bucket is like a virtual file folder in the cloud where you can store various types of data, such as text files, images, videos, and more. There is no limit to the amount of data you can store in an S3 bucket, and individual instances can be up to 5 TB in size.
In this case we don’t know who’s behind the leak, although it seems clear from the screenshots that it’s a phishing operation and the credit and debit card information was exactly the data they were after. Although they probably didn’t intend to share it with the whole world.
Unfortunately, not knowing who left the data exposed makes it harder to plug the hole, but the AWS Abuse team initiated an investigation based on the information provided by Leakd.
The leaked information contains 5 terabytes of screenshots where victims filled out their details on websites that offered “free iPhones” and heavily discounted holiday gifts.
Looking at how those screenshots are organized, there are two possible sources.
- Information stealers, many infostealers are capable of taking screenshots and naming them in a way that helps the attackers track and organize the stolen data.
- Phishing using websites that were especially set up for this task. This seems to most likely scenario, because of the content of the screenshots.
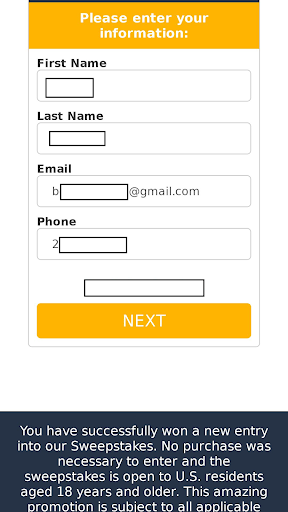
As Leakd.com describes it:
“The leaked screenshots often featured instances of users entering personal and financial details into seemingly innocent promotional forms.”
What do I need to do?
Stolen payment card details are bad enough, as they can be used for financial fraud, identity theft, and cause privacy issues.
The timing just weeks before Christmas makes it even worse. It is hard enough to keep track of your own spending for some of us, let alone when a criminal decides to spend some of our money. And having to cancel your payment card because someone else might use it is most inconvenient right now.
But if you suspect that your payment card details have been stolen, these are the recommended actions:
- Regularly check account and card statements and notify your bank about any suspicious activity.
- Where possible, set up fraud alerts with your bank or payment card provider.
- Change the password and enable multi-factor authentication if you haven’t already.
- Freeze your credit so nobody can open any new accounts in your name.
If you don’t want to become a victim of these cybercriminals:
- Don’t get phished. Be aware of the signs and don’t respond to unsolicited emails and texts.
- Shy away from sites making too-good-to-be-true offers.
- Use web protection like Malwarebytes Browser Guard. It flags malicious websites and credit card skimmers that steal your information.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>An unfamiliar type of scam has surged against everyday people, with a year-over-year increase of some 400%, putting job seekers at risk of losing their time and money.
The emerging threat is delivered in “task scams” or “gamified job scams.” While these scams were virtually non-existent in 2020, the FTC reported 5,000 cases in 2023 and a whopping 20,000 cases in the first half of 2024.
In these scams, online criminals prey on people looking for remote jobs by offering them simple repetitive tasks such as liking videos, optimizing apps, boosting product interest, or rating product images. These tasks are usually organized in sets of 40 tasks that will take the victim to a “next level” once they are completed.
Sometimes the victim will get a so-called double task that earns a bigger commission. The trick is that the scammers will make the victim think they are earning money to raise trust in the system. The money can be fake and only displayed in the system, but some victims report actually receiving small sums.
But at some point, the scammers will tell the victims, they have to make a deposit to get the next set of tasks or get your earnings out of the app. So, victims are likely to make that deposit, or all their work will have been for naught.
Scammers use cryptocurrency like USDT (a digital stable-coin with a value tied to the value of the US dollar) to make their payments.
Task scams typically begin with unsolicited text messages or messages via platforms like WhatsApp, Telegram, or other messaging apps. These messages often come from unknown numbers or profiles that may appear professional to gain trust. Reportedly, these scams like to impersonate legitimate companies such as Deloitte, Amazon, McKinsey and Company, and Airbnb.
Scammers count on the urge that victims do not want to “cut their losses” and will try to pull victims in even deeper, sometimes inviting them into groups where newcomers can learn and hear success stories from (fake) experienced workers.
How to avoid task scams
Once you know the red flags, it is easier to shy away from task scams.
- Do not respond to unsolicited job offers via text messages or messaging apps.
- Never pay to get paid.
- Verify the legitimacy of the employer through official channels.
- Don’t trust anyone who offers to pay you for something illegal such as rating or liking things online.
It’s also important to keep in mind that legitimate employers do not ask employees to pay for the opportunity to work. And as with most scams, if it sound to good to be true, it probably is.
If you run into a task scam, please report them to the FTC at ReportFraud.ftc.gov.
]]>This week on the Lock and Code podcast…
Privacy is many things for many people.
For the teenager suffering from a bad breakup, privacy is the ability to stop sharing her location and to block her ex on social media. For the political dissident advocating against an oppressive government, privacy is the protection that comes from secure, digital communications. And for the California resident who wants to know exactly how they’re being included in so many targeted ads, privacy is the legal right to ask a marketing firm how they collect their data.
In all these situations, privacy is being provided to a person, often by a company or that company’s employees.
The decisions to disallow location sharing and block social media users are made—and implemented—by people. The engineering that goes into building a secure, end-to-end encrypted messaging platform is done by people. Likewise, the response to someone’s legal request is completed by either a lawyer, a paralegal, or someone with a career in compliance.
In other words, privacy, for the people who spend their days with these companies, is work. It’s their expertise, their career, and their to-do list.
But what does that work actually entail?
Today, on the Lock and Code podcast with host David Ruiz, we speak with Transcend Field Chief Privacy Officer Ron de Jesus about the responsibilities of privacy professionals today and how experts balance the privacy of users with the goals of their companies.
De Jesus also explains how everyday people can meaningfully judge whether a company’s privacy “promises” have any merit by looking into what the companies provide, including a legible privacy policy and “just-in-time” notifications that ask for consent for any data collection as it happens.
“When companies provide these really easy-to-use controls around my personal information, that’s a really great trigger for me to say, hey, this company, really, is putting their money where their mouth is.”
Tune in today to listen to the full conversation.
Show notes and credits:
Intro Music: “Spellbound” by Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 4.0 License
http://creativecommons.org/licenses/by/4.0/
Outro Music: “Good God” by Wowa (unminus.com)
Listen up—Malwarebytes doesn’t just talk cybersecurity, we provide it.
Protect yourself from online attacks that threaten your identity, your files, your system, and your financial well-being with our exclusive offer for Malwarebytes Premium for Lock and Code listeners.
]]>Last week on Malwarebytes Labs:
- Encrypted messaging service intercepted, 2.3 million messages read by law enforcement
- TikTok ban in US: Company seeks emergency injunction to prevent it
- Data brokers should stop trading health and location data, new bill proposes
- Update now! Apple releases new security patches for vulnerabilities in iPhones, Macs, and more
- 4.8 million healthcare records left freely accessible
- Malicious ad distributes SocGholish malware to Kaiser Permanente employees
Last week on ThreatDown:
- 2024 MITRE ATT&CK® Evaluation results: ThreatDown detected every step
- December patch Tuesday fixes one actively exploited zero-day vulnerability
- What is Cross-Site Request Forgery (CSRF)?
Stay safe!
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
]]>On December 15, we detected a malicious campaign targeting Kaiser Permanente employees via Google Search Ads. The fraudulent ad masquerades as the health care company’s HR portal used to check for benefits, download paystubs and other corporate related tasks.
We believe the threat actors’ intent was to phish KP employees for their login credentials, but something unexpected happened. Instead, victims who clicked on the ad were redirected to a compromised website that prompted them to update their browser.
This notification is part of a malware campaign known as SocGholish that tricks users into running a script supposedly meant to update their browser. Rather, it infects machines and if the victim is deemed important enough, a human operator will gain access in order to perform nefarious actions.
In this blog post, we review how this attack unfolds and why a compromised website derailed the attackers’ plan. We already reported the malicious ad to Google.
Malicious Kaiser Permanente ad
Several criminal gangs are currently abusing Google Ads to phish victims of various large companies. They prey on employees simply googling for their HR portal so that they can display a malicious ad to lure them in.
Case in point, when searching for Kaiser Permanente’s HR portal, we saw the following ad:

We were able to identify the advertiser who registered a fake account under the name ‘Heather Black’. This ad was only showed for U.S.-based searches, as can be seen in the Google Ads Transparency Center report:

Former company’s website hijacked for phishing
The displayed url shown in the ad (https://www.bellonasoftware[.]com) does not look associated with Kaiser Permanente. According to LinkedIn, Bellona Software was a company based in Romania. We can see what their website looked like in 2021, using the Internet Archive:

Some time more recently, this same website was taken over by criminals who transformed it into a phishing page for Kaiser Permanente:

Malicious redirect to SocGholish
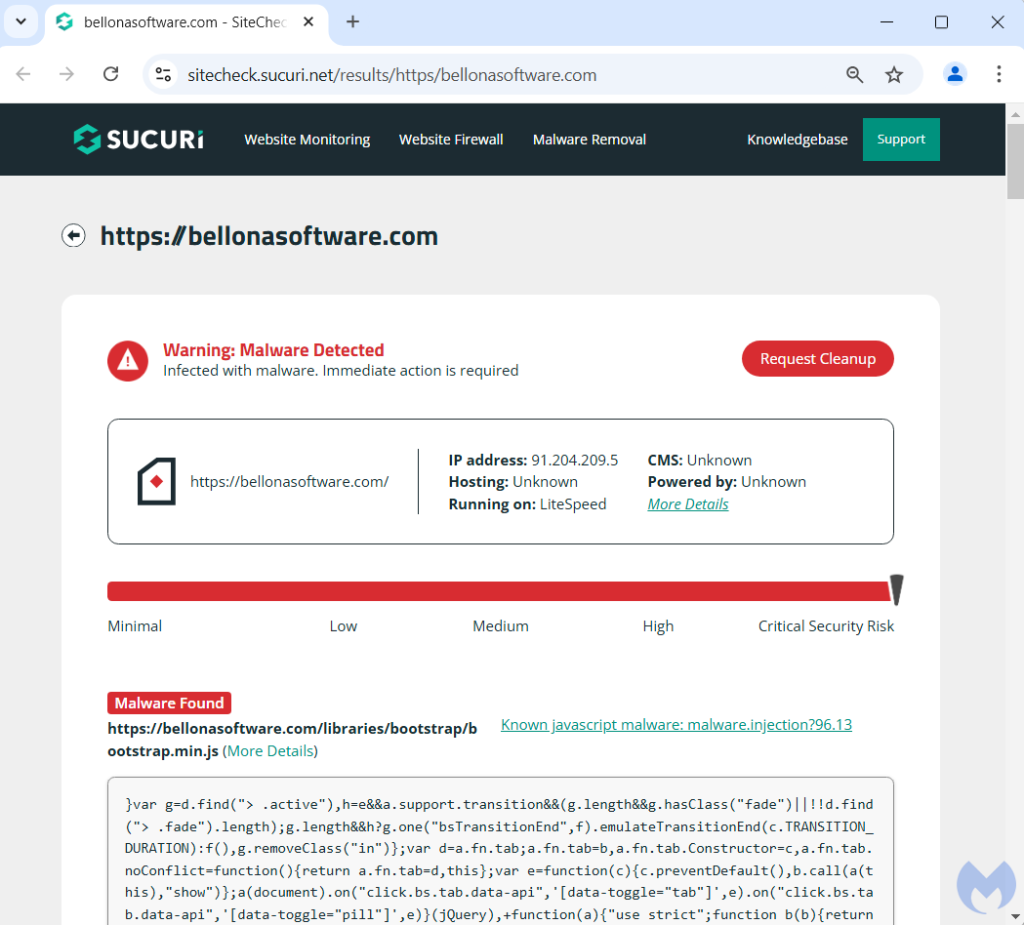
It looks like there was more than one cook in the kitchen, as malicious code was also injected in the core JavaScript libraries for that website, confirmed in a scan by Sucuri’s SiteCheck:
When potential victims clicked on the ad, they landed on that compromised website, which in turn briefly displayed the phishing template only for as long as a mouse scroll or click. Then, a new screen appeared with what looks like a Google Chrome notification claiming the user’s browser is out of date:

This screen, also known as SocGholish, is a long running malware campaign that targets vulnerable websites indiscriminately. When a user executes the downloaded Update.js file, they are instead running a malicious script that will collect some of their computer’s information and relay it to a group of criminals. After this fingerprinting takes place, additional tooling such as Cobalt Strike may be downloaded, preparing the ground for a human on keyboard type of attack.
To the best of our knowledge, the phishing campaign has nothing to do with SocGholish, and we assume that the original threat actors did not anticipate for the website they took over to be compromised. As for the gang behind SocGholish, the victims would come from a Google search, something they usually check for via the referer.
Protecting against web threats
For victims, neither the phishing scheme nor the malware are a happy outcome. While initially targeted because of what they searched for, they fell into the hands of a different criminal syndicate.
Such is the reality of web threats. This is a dynamic and ever changing landscape with a number of malicious players trying to lure users in their own way.
Online ads, and in particular search ads, continue to be a threat. As we have showed many times on this blog, any brand is at risk of being impersonated. Unfortunately, this trend has continued unabated throughout 2024.
At the same time, ‘old’ malware campaigns like SocGholish pose a risk due to a never ending number of outdated websites ready to be compromised and act as a springboard for malware delivery.
When searching online, we urge to use extreme caution with any sponsored results and if possible add protection to your online browsing experience with tools like Malwarebytes Browser Guard.
We reported the malicious ad to Google and will update this blog if we hear anything back.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
Indicators of Compromise
Phishing site
bellonasoftware[.]com
SocGholish infrastructure
premium[.]davidabostic[.]com]]>
riders[.]50kfor50years[.]com
Your main business is healthcare, so your excuse when you get hacked is that you didn’t have the budget to secure your network. Am I right?
So, in order to prevent a ransomware gang from infiltrating your network, you could just give them what they want—all your data.
The seemingly preferred method to accomplish this is to leave the information unprotected and unencrypted in an exposed Amazon S3 bucket.
An S3 bucket is like a virtual file folder in the cloud where you can store various types of data, such as text files, images, videos, and more. There is no limit to the amount of data you can store in an S3 bucket, and individual instances can be up to 5 TB in size.
Security researcher Jeremiah Fowler is always looking for exposed cloud storage. And recently he found one that contained over 4.8 million documents with a total size of 2.2 TB.
He soon found out that it belonged to a Canadian company offering AI software solutions to support optometrists in delivering enhanced patient care, called Care1. Care1 Canada provides software tools that “take patient care to the next level.”
The information Jeremiah found included eye exam results, which detailed patient PII, doctor’s comments, and images of the exam results. The database also contained lists of patients which included their home addresses, Personal Health Numbers (PHN), and details regarding their health.
In the Canadian healthcare system, a Personal Health Number (PHN) is a unique lifetime identifier that is used to share a patient’s health information among healthcare providers.
This type of healthcare information can be used in phishing attacks, identity theft, and can cause health privacy issues. Ransomware gangs know this is highly coveted, which is why ThreatDown numbers regularly show that 5 to 6% of ransomware attacks are targeting the healthcare industry.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
]]>