ã“ã‚“ã«ã¡ã¯ã€‚GMOインターãƒãƒƒãƒˆ 新里ã§ã™ã€‚
組込ã¿ãƒ»IoTçš„ãªç«¯æœ«ã§ã‚ˆã利用ã•ã‚Œã¦ã„ã‚‹mbedTLSã®æœ€æ–°ãƒãƒ¼ã‚¸ãƒ§ãƒ³ã‚’使ã£ã¦ã€TLS 1.3〜QUICã®æš—å·åŒ–ã¾ã§å®Ÿéš›ã«ESP32を利用ã—ã¦è¡Œã£ã¦ã¿ã¾ã™ã€‚
目次
mbedTLS
mbedTLS ã¯çµ„è¾¼ã¿æ©Ÿå™¨ãªã©ã§ä½¿ã‚れるコンパクトãªã‚µã‚¤ã‚ºã®SSL/TSLライブラリã§ã™ã€‚よã知られã¦ã„ã‚‹SSLライブラリã§ã¯OpenSSL/BoringSSLãªã©ãŒã‚ã‚Šã¾ã™ã。ãŸã ã€IoTçš„ãªç«¯æœ«ãªã©ã§ã¯ã‚¹ãƒšãƒƒã‚¯ãŒé™ã‚‰ã‚ŒãŸã‚‚ã®ã«ãªã‚Šã¾ã™ã€‚例ãˆã°ã€åƒ•ãŒåˆ©ç”¨ã™ã‚‹ç«¯æœ«ã ã¨ã‚¢ãƒ—リケーションを組込ã‚ã‚‹é ˜åŸŸãŒã‚ãšã‹256Kbyteã¨ã„ã†ã‚µã‚¤ã‚ºã¨ã‹ã ã£ãŸã‚Šã—ã¾ã™ã€‚
ãã†ã„ã£ãŸIoTçš„ãªæ©Ÿå™¨ã‚„組込ã¿æ©Ÿå™¨ã®ã‚ˆã†ãªã‚¹ãƒšãƒƒã‚¯ã§ã€PCやサーãƒãƒ¼ã§åˆ©ç”¨ã•ã‚Œã¦ã„るよã†ãªSSL/TLSライブラリを組込んã§ä½¿ã†ã®ã¯ã‚¹ãƒšãƒƒã‚¯çš„ã«ã‚‚難ã—ã„ã§ã™ã€‚ãã“ã§ä½¿ã‚れるã®ãŒçµ„è¾¼ã¿ç«¯æœ«å‘ã‘ã®ã‚³ãƒ³ãƒ‘クトãªãƒ©ã‚¤ãƒ–ラリã¨ã„ã†ã‚ã‘ã§ã™ã€‚
mbedTLSã®ä»–ã«ã‚‚組込ã¿æ©Ÿå™¨å‘ã‘をターゲットã«ã—ãŸSSL/TSLライブラリ㫠wolfSSL ã‚‚ã‚ã‚Šã¾ã™ã€‚個人的ã«ã¯mbedTLSã€wolfSSLã¯çµ„è¾¼ã¿æ©Ÿå™¨å‘ã‘OSS SSL/TLSã§ã‚ˆã見るもã®ã§ã™ã€‚
æ°—ãŒã¤ã„ãŸã‚‰…
ãã‚“ãªmbedTLSを組込ã¿ã§åˆ©ç”¨ã—ã¦ã„ã¦ã€æ°—ãŒã¤ã„ãŸã‚‰ãƒãƒ¼ã‚¸ãƒ§ãƒ³ãŒ3.1.0ã«ãªã£ã¦ã„ã¾ã—ãŸã€‚ä»–ã«ã‚‚ãƒãƒ¼ã‚¸ãƒ§ãƒ³ãŒä½•å€‹ã‹ã‚ã£ã¦ã€ç¾æ™‚点ã§ã¯…
・2.16.x :Long Time Supportã®æœ€å¾Œã®ãƒãƒ¼ã‚¸ãƒ§ãƒ³ã€‚2.28ç³»ã¸ã®ç§»è¡Œã‚’勧ã‚る。
・2.28.x :2024年末ã¾ã§ãƒã‚°ãƒ»ã‚»ã‚ュリティフィックスã®ã‚µãƒãƒ¼ãƒˆãŒè¡Œã‚れる。
・3.1.x  :最新ã®ãƒã‚°ãƒ»ã‚»ã‚ュリティフィックスã€æ©Ÿèƒ½è¿½åŠ ãŒè¡Œã‚れる。
僕ãŒå€‹äººçš„ã«ãƒ¡ãƒ³ãƒ†ã—ã¦ã„るライブラリã§ã¯2.16系を使ã£ã¦ã„ãŸã®ã§ã€ã¨ã‚Šã‚ãˆãš2.28.0ã«ã‚¢ãƒƒãƒ—デートã—ã¾ã—ãŸã€‚ã“ã®ã¨ãã€PSA(Platform Security Architecture)ã¨ã„ã†ãƒ¢ã‚¸ãƒ¥ãƒ¼ãƒ«ã‚»ãƒƒãƒˆãŒè¿½åŠ ã•ã‚Œã¦å…¨ä½“çš„ã«ãƒ‰ãƒ©ã‚¹ãƒ†ã‚£ãƒƒã‚¯ã«æ§‹æˆãŒå¤‰ã‚ã£ã¦ã„ã¦ã€ã“れらを組込むã®ãŒåœ°å‘³ã«é¢å€’ã§ã—ãŸã€‚
ãŸã ã€2.28.xç³»ã¯ã‚ã¨2å¹´å¼±ã§ã‚µãƒãƒ¼ãƒˆå¯¾è±¡ã‹ã‚‰å¤–ã‚Œã¦ã—ã¾ã†ã¨ã„ã†äº‹ã‚‚ã‚ã£ã¦ã€ä»Šå¾Œã®ã‚¢ãƒƒãƒ—デートを考ãˆã‚‹ã¨æœ€æ–°ã®3.1系を追ã„ã‹ã‘ãŸæ–¹ãŒè‰¯ã•ãã†ã§ã™ã€‚
mbedTLS 3.1系を見ã¦ã¿ã‚‹
mbedTLSã¯config(ヘッダファイル)ã§åˆ©ç”¨ã™ã‚‹ã‚¢ãƒ«ã‚´ãƒªã‚ºãƒ ã‚’è¨å®šã™ã‚‹ã“ã¨ãŒå‡ºæ¥ã¾ã™ã€‚例ãˆã°ã€DTLSを使ã„ãŸã‹ã£ãŸã‚‰”#define MBEDTLS_SSL_PROTO_DTLS”を書ã„ã¦ãŠãã¨ã„ã£ãŸæ„Ÿã˜ã§ã™ã€‚mbedTLS 3.1ç³»ã§ã¯è«¸ã€…ã®è¨å®šãŒæ›¸ã„ã¦ã‚ã‚‹ã®ã¯ mbedtls_confi.h ã«ãªã£ã¦ã„ã¾ã—ãŸã€‚ã–ã£ã¨è¦‹ã¦ã¿ã¦å€‹äººçš„ã«ãŠã‚„?ã¨æ€ã£ãŸç‚¹ã¯ã“ã®è¾ºã§ã™ã€‚
・MBEDTLS_SSL_PROTO_TLS1_3ãŒå…¥ã£ã¦ããŸã€‚
・TLS 1.0/1.1, 3DES, MD2, MD5, RC4, Blowfish, XTEAãŒç„¡ããªã£ãŸã€‚
・PSA周りã®è¨å®šãŒå¢—ãˆã¦ã„ãŸã€‚
MBEDTLS_SSL_PROTO_TLS1_3_EXPERIMENTALã ã£ãŸã®ãŒã€EXPERIMENTALãŒå–ã‚Œã¦ã„ã¾ã—ãŸã€‚ã“ã‚Œã‹ã‚‰çµ„è¾¼ã¿ã‚‚TLS 1.3ã«å‘ã‹ã£ã¦ã„ããž!!ã¨ã„ã†æ°—æŒã¡ã‚’æ„Ÿã˜ã¾ã™ã€‚
TLS 1.3ã‚’PC上ã§ä½¿ã£ã¦ã¿ã‚‹
ç¾æ™‚点ã§ã®æœ€æ–°ç‰ˆ mbedTLS 3.10 ã‚’ã¨ã‚Šã‚ãˆãšãƒ“ルドã—ã¦ã‚µãƒ³ãƒ—ルプãƒã‚°ãƒ©ãƒ 経由ã§ã€www.google.com ã«TLS 1.3ã§ã‚¢ã‚¯ã‚»ã‚¹ã—ã¦ã¿ã¾ã™ã€‚(環境ã¯Macを利用ã—ã¦ã„ã¾ã™ã€‚ビルドエラーã§å¿…è¦ãªç‰©ã¯é©å®œbrewã§å…¥ã‚Œã¾ã™ã€‚)
wget https://github.com/Mbed-TLS/mbedtls/archive/refs/tags/v3.1.0.tar.gz
tar -zxvf v3.1.0.tar.gz
cd mbedtls-3.1.0
# include/mbedtls/mbedtls_config.h ã‹ã‚‰
# MBEDTLS_SSL_PROTO_TLS1_3
# MBEDTLS_SSL_TLS1_3_COMPATIBILITY_MODE
# をコメントアウトã—ã¦ãƒ“ルド
make
# www.google.com ã«æŽ¥ç¶šã—ã¦ã¿ã‚‹ã€‚Root CAをダウンãƒãƒ¼ãƒ‰
wget https://pki.goog/repo/certs/gtsr1.pem
# force_version=tls13 を付ã‘ã¦TLS 1.3ã§ã‚¢ã‚¯ã‚»ã‚¹
./programs/ssl/ssl_client2 server_name=www.google.com server_port=443 ca_file=./gtsr1.pem force_version=tls13ã“ã®ã¨ãã€æœ¬å½“ã«TLS 1.3ã§ã‚¢ã‚¯ã‚»ã‚¹ã—ã¦ã„ã‚‹ã®ã‹ï¼ŸWiresharkを使ã£ã¦åŒæ™‚ã«è¦³æ¸¬ã—ã¾ã™ã€‚
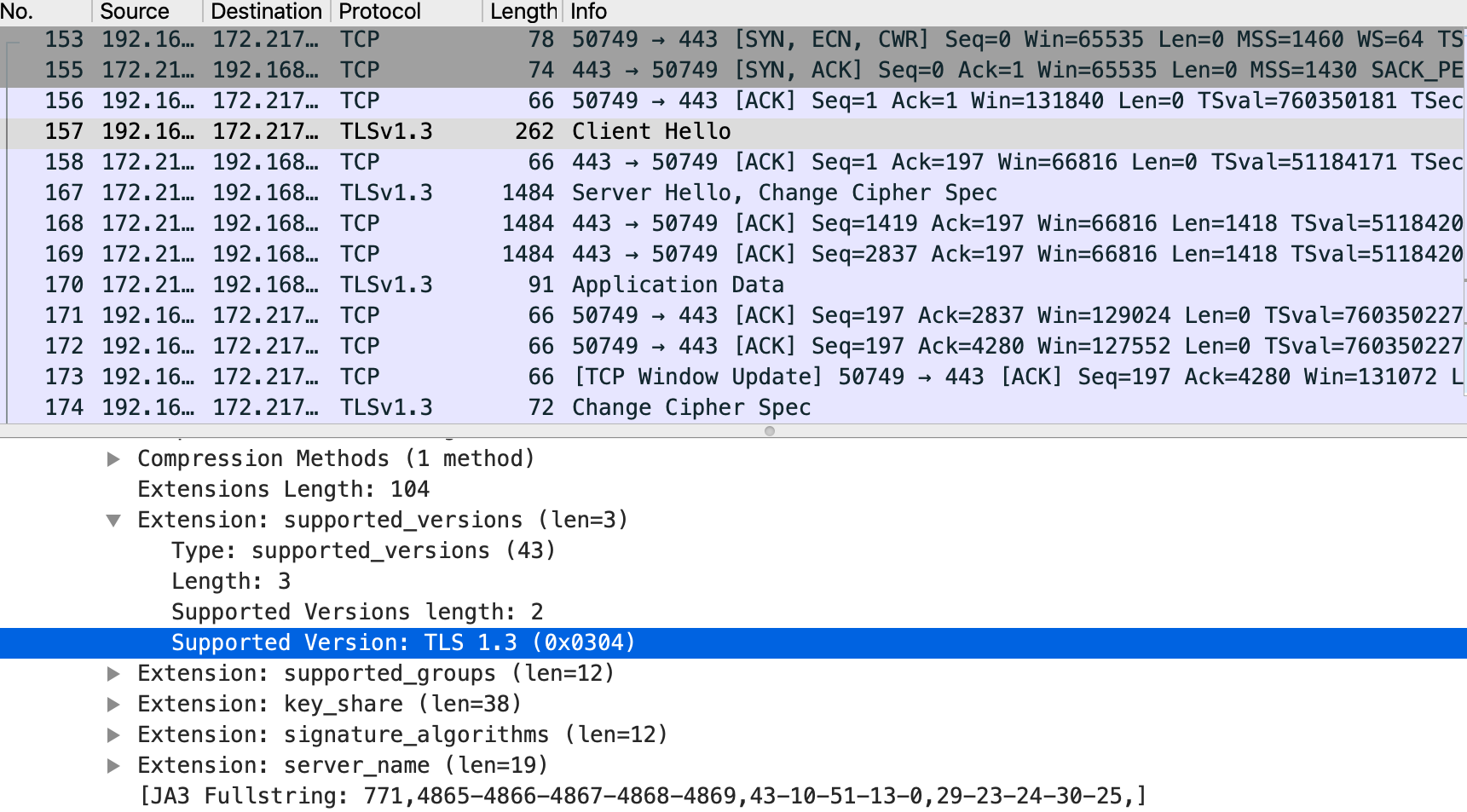
TLS 1.3ã§ã‚¢ã‚¯ã‚»ã‚¹ã—ã¦ã„るよã†ã§ã™ã€‚1-RTTã§çµ‚ã‚ã‚‹ã¯ãšãŒã€ãªãœã‹ã‚¯ãƒ©ã‚¤ã‚¢ãƒ³ãƒˆå´ã‹ã‚‰Change Cipher SpecãŒé£›ã‚“ã§ã„ã¾ã™ã€‚ã“ã‚Œã¯MBEDTLS_SSL_TLS1_3_COMPATIBILITY_MODE ã®èª¬æ˜Žã«ã‚る通り(RFC 8446 D.4. Middlebox Compatibility Mode)ã€ãƒŸãƒ‰ãƒ«ãƒœãƒƒã‚¯ã‚¹ã®ä¸‹ä½äº’æ›æ€§ã®ãŸã‚ã«æŠ•ã’ã¦ã„る空ã®Change Cipher Specã§ã™ã。
ESP32ã‹ã‚‰TLS 1.3を使ã£ã¦ã¿ã‚‹
ã¨ã‚Šã‚ãˆãšTLS 1.3ã§é€šä¿¡ãŒå‡ºæ¥ãŸã®ã§ã€å®Ÿéš›ã«çµ„è¾¼ã¿ã§ä½¿ã„ãŸããªã‚‹ã®ã¯äººã®æ€§ã§ã—ょã†ã€‚
ã“ã“ã§ã¯ESP32 Devboardã‹ã‚‰ã‚¢ã‚¯ã‚»ã‚¹ã—ã¦ä½¿ã£ã¦ã¿ã¾ã™ã€‚ã¨ã„ã†ã®ã‚‚ã€ESP32 IDF(Arduino IDEã§ã‚‚)ã§ã¯mbedTLSãŒåˆ©ç”¨ã•ã‚Œã¦ã„ã¦ã€ã¨ã‚Šã‚ãˆãšå‹•ã‹ã—ã¦ã¿ã‚‹ã®ã«ã¯ã¡ã‚‡ã†ã©è‰¯ã‹ã£ãŸã®ã‚‚ã‚ã‚Šã¾ã™ã€‚
ã“ã“ã§åˆ©ç”¨ã™ã‚‹ã®ã¯ã€ESP-WROOM-32ブレイクアウトSD+ã§ã™ã€‚

ESP-IDF ã®mbedTLSã®çµ„è¾¼ã¿å®Ÿè£…を見ã¦ã¿ãŸã¨ã“ã‚ã€ãƒªãƒã‚¸ãƒˆãƒªã®æœ€æ–°ã¯æ—¢ã«3.1.0å‘ã‘ã«ãªã£ã¦ã„ã¾ã—ãŸã€‚releaseãƒãƒ¼ã‚¸ãƒ§ãƒ³ã§ã¯ã¾ã ã§ã™ãŒã€ä»Šå¾Œã¯ESP32ã®TLSã§ã‚‚mbedTLS 3.1ç³»ãŒåˆ©ç”¨ã•ã‚Œã‚‹ã“ã¨ãŒæƒ³åƒã•ã‚Œã¾ã™ã€‚
ã¨ã‚Šã‚ãˆãš esp-idf 経由ã§å…ˆç¨‹ã¨åŒã˜ã www.google.com ã«TLS1.3ã§ã‚¢ã‚¯ã‚»ã‚¹ã—ã¦ã¿ã¾ã™ã€‚
# release ãƒãƒ¼ã‚¸ãƒ§ãƒ³ã§ã¯ãªãã€æœ€æ–°ã®repoã‹ã‚‰å…¨éƒ¨å–å¾—ã—ã¦ãる。
git clone --recursive https://github.com/espressif/esp-idf.git
cd esp-idf
# esp-idf ã®ç’°å¢ƒæ§‹ç¯‰æ‰‹é †
# https://docs.espressif.com/projects/esp-idf/en/latest/esp32/get-started/linux-macos-setup.html
# æ‰‹é †ã«å¾“ã£ã¦ç’°å¢ƒã‚’準備ã™ã‚‹ã€‚
# å¿…è¦ãªãƒ‘ãƒƒã‚±ãƒ¼ã‚¸ã‚’ã‚¤ãƒ³ã‚¹ãƒˆãƒ¼ãƒ«ãƒ»æ‰‹é †ã«å¾“ã£ã¦ãƒ“ルド環境を整備ã™ã‚‹ã€‚
# ã“ã“ã‹ã‚‰ãŒæœ¬ç•ª
cp -r examples/protocols/https_mbedtls/ .
cd https_mbedtls
idf.py set-target esp32
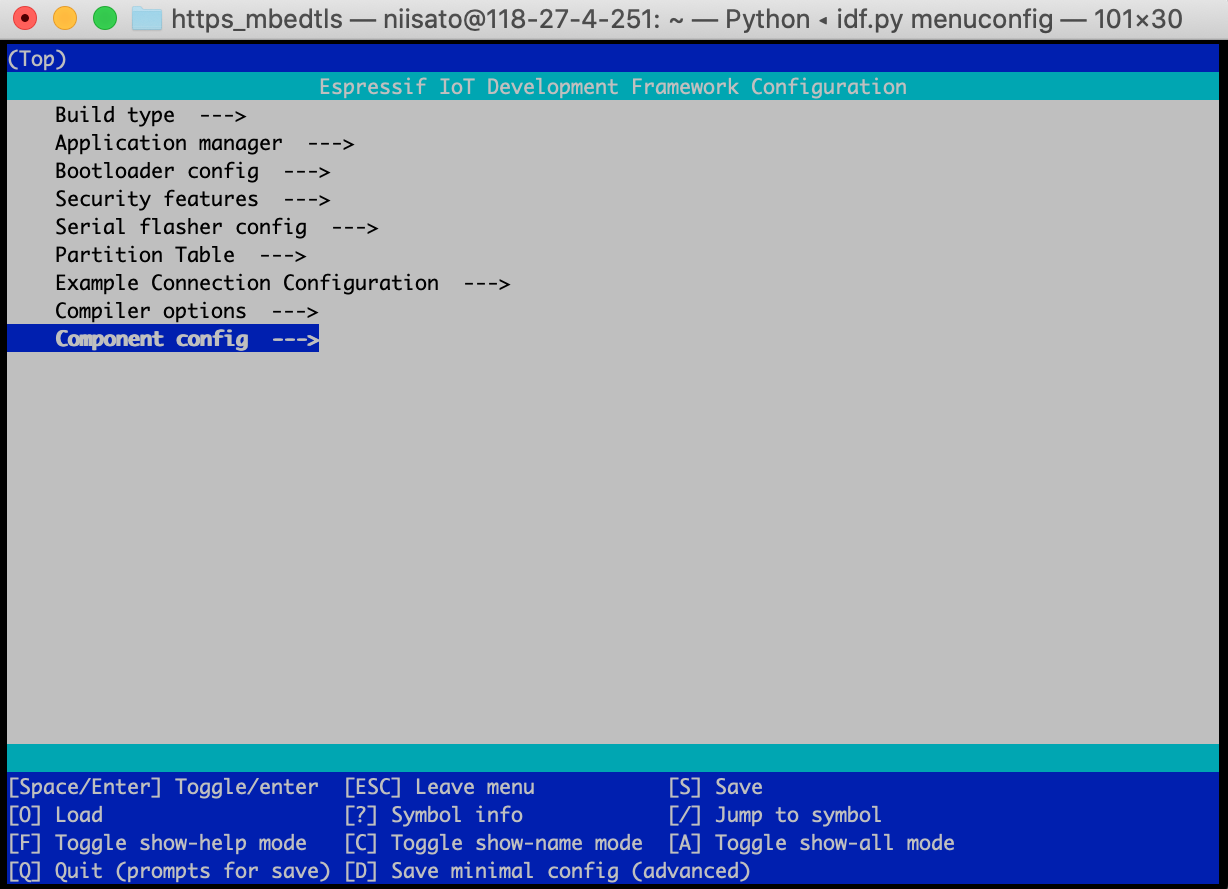
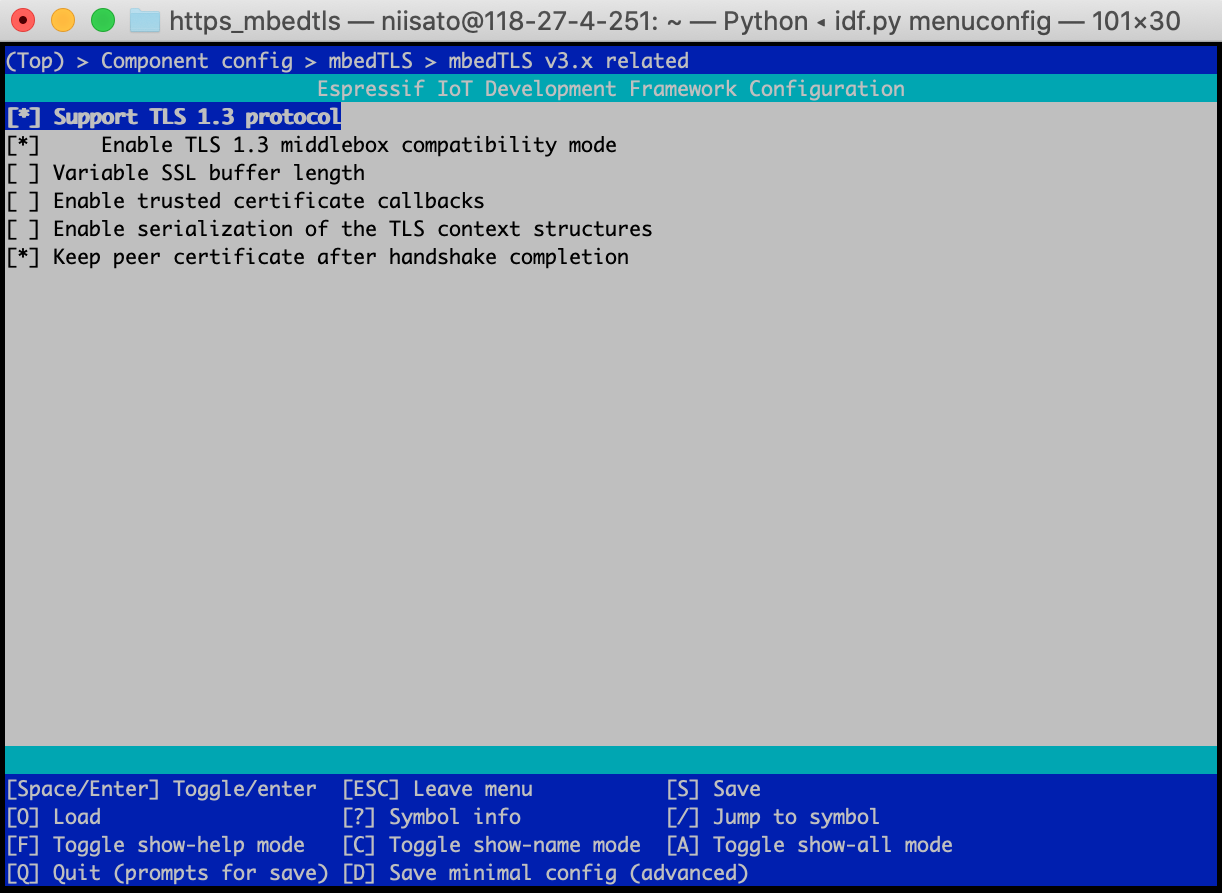
idf.py menuconfigPC上ã§ã¯mbedTLSã®configを直接変更ã—ã¾ã—ãŸãŒã€esp idfã§ã¯menuconfigã‹ã‚‰è¨å®šã™ã‚‹ã“ã¨ãŒå‡ºæ¥ã¾ã™ã€‚menuconfigã® â€Component config†-> “mbedTLS†-> “mbedTLS v3.x related†-> “Support TLS 1.3 protocol†を有効ã«ã—ã¾ã™ã€‚ã“ã®æ™‚ã€WiFiã®æŽ¥ç¶šè¨å®šã‚‚ â€Example Connection Configuration†ã‹ã‚‰è¡Œã£ã¦ã€NWã«æŽ¥ç¶šã§ãるよã†ã«ã—ã¦ãŠã。
次ã«ã‚½ãƒ¼ã‚¹ã‚³ãƒ¼ãƒ‰ã‚’å°‘ã—ä¿®æ£ã—ã¾ã™ã€‚ã“ã®ã¾ã¾ã ã¨TLS 1.2ã§æŽ¥ç¶šã™ã‚‹ã®ã§ã€ã‚µãƒ³ãƒ—ル㮠https_mbedtls_example_main.c を以下ã®ã‚ˆã†ã«ä¿®æ£ã—ã¾ã™ã€‚サンプルコードãªã®ã§å…¨ä½“を載ã›ã¦ãŠãã¾ã™ã€‚
#include <string.h>
#include <stdlib.h>
#include "freertos/FreeRTOS.h"
#include "freertos/task.h"
#include "esp_wifi.h"
#include "esp_event.h"
#include "esp_log.h"
#include "esp_system.h"
#include "nvs_flash.h"
#include "protocol_examples_common.h"
#include "esp_netif.h"
#include "lwip/err.h"
#include "lwip/sockets.h"
#include "lwip/sys.h"
#include "lwip/netdb.h"
#include "lwip/dns.h"
#include "mbedtls/platform.h"
#include "mbedtls/net_sockets.h"
#include "mbedtls/esp_debug.h"
#include "mbedtls/ssl.h"
#include "mbedtls/entropy.h"
#include "mbedtls/ctr_drbg.h"
#include "mbedtls/error.h"
#include "esp_crt_bundle.h"
// 接続先ã¯Google
#define WEB_SERVER "www.google.com"
#define WEB_PORT "443"
#define WEB_URL "/"
static const char *TAG = "example";
static const char *REQUEST = "GET " WEB_URL " HTTP/1.0\r\n"
"Host: "WEB_SERVER"\r\n"
"User-Agent: esp-idf/1.0 esp32\r\n"
"\r\n";
// GTS Root R1 ã®PEMã‚’å–ã£ã¦ãã¦ç½®ã„ã¨ã
#define GTSR1_CA_PEM \
"-----BEGIN CERTIFICATE-----\r\n" \
"MIIFVzCCAz+gAwIBAgINAgPlk28xsBNJiGuiFzANBgkqhkiG9w0BAQwFADBHMQsw\r\n" \
"CQYDVQQGEwJVUzEiMCAGA1UEChMZR29vZ2xlIFRydXN0IFNlcnZpY2VzIExMQzEU\r\n" \
"MBIGA1UEAxMLR1RTIFJvb3QgUjEwHhcNMTYwNjIyMDAwMDAwWhcNMzYwNjIyMDAw\r\n" \
"MDAwWjBHMQswCQYDVQQGEwJVUzEiMCAGA1UEChMZR29vZ2xlIFRydXN0IFNlcnZp\r\n" \
"Y2VzIExMQzEUMBIGA1UEAxMLR1RTIFJvb3QgUjEwggIiMA0GCSqGSIb3DQEBAQUA\r\n" \
"A4ICDwAwggIKAoICAQC2EQKLHuOhd5s73L+UPreVp0A8of2C+X0yBoJx9vaMf/vo\r\n" \
"27xqLpeXo4xL+Sv2sfnOhB2x+cWX3u+58qPpvBKJXqeqUqv4IyfLpLGcY9vXmX7w\r\n" \
"Cl7raKb0xlpHDU0QM+NOsROjyBhsS+z8CZDfnWQpJSMHobTSPS5g4M/SCYe7zUjw\r\n" \
"TcLCeoiKu7rPWRnWr4+wB7CeMfGCwcDfLqZtbBkOtdh+JhpFAz2weaSUKK0Pfybl\r\n" \
"qAj+lug8aJRT7oM6iCsVlgmy4HqMLnXWnOunVmSPlk9orj2XwoSPwLxAwAtcvfaH\r\n" \
"szVsrBhQf4TgTM2S0yDpM7xSma8ytSmzJSq0SPly4cpk9+aCEI3oncKKiPo4Zor8\r\n" \
"Y/kB+Xj9e1x3+naH+uzfsQ55lVe0vSbv1gHR6xYKu44LtcXFilWr06zqkUspzBmk\r\n" \
"MiVOKvFlRNACzqrOSbTqn3yDsEB750Orp2yjj32JgfpMpf/VjsPOS+C12LOORc92\r\n" \
"wO1AK/1TD7Cn1TsNsYqiA94xrcx36m97PtbfkSIS5r762DL8EGMUUXLeXdYWk70p\r\n" \
"aDPvOmbsB4om3xPXV2V4J95eSRQAogB/mqghtqmxlbCluQ0WEdrHbEg8QOB+DVrN\r\n" \
"VjzRlwW5y0vtOUucxD/SVRNuJLDWcfr0wbrM7Rv1/oFB2ACYPTrIrnqYNxgFlQID\r\n" \
"AQABo0IwQDAOBgNVHQ8BAf8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4E\r\n" \
"FgQU5K8rJnEaK0gnhS9SZizv8IkTcT4wDQYJKoZIhvcNAQEMBQADggIBAJ+qQibb\r\n" \
"C5u+/x6Wki4+omVKapi6Ist9wTrYggoGxval3sBOh2Z5ofmmWJyq+bXmYOfg6LEe\r\n" \
"QkEzCzc9zolwFcq1JKjPa7XSQCGYzyI0zzvFIoTgxQ6KfF2I5DUkzps+GlQebtuy\r\n" \
"h6f88/qBVRRiClmpIgUxPoLW7ttXNLwzldMXG+gnoot7TiYaelpkttGsN/H9oPM4\r\n" \
"7HLwEXWdyzRSjeZ2axfG34arJ45JK3VmgRAhpuo+9K4l/3wV3s6MJT/KYnAK9y8J\r\n" \
"ZgfIPxz88NtFMN9iiMG1D53Dn0reWVlHxYciNuaCp+0KueIHoI17eko8cdLiA6Ef\r\n" \
"MgfdG+RCzgwARWGAtQsgWSl4vflVy2PFPEz0tv/bal8xa5meLMFrUKTX5hgUvYU/\r\n" \
"Z6tGn6D/Qqc6f1zLXbBwHSs09dR2CQzreExZBfMzQsNhFRAbd03OIozUhfJFfbdT\r\n" \
"6u9AWpQKXCBfTkBdYiJ23//OYb2MI3jSNwLgjt7RETeJ9r/tSQdirpLsQBqvFAnZ\r\n" \
"0E6yove+7u7Y/9waLd64NnHi/Hm3lCXRSHNboTXns5lndcEZOitHTtNCjv0xyBZm\r\n" \
"2tIMPNuzjsmhDYAPexZ3FL//2wmUspO8IFgV6dtxQ/PeEMMA3KgqlbbC1j+Qa3bb\r\n" \
"bP6MvPJwNQzcmRk13NfIRmPVNnGuV/u3gm3c\r\n" \
"-----END CERTIFICATE-----"
const unsigned char gtsr1_pem[] = GTSR1_CA_PEM;
static void https_get_task(void *pvParameters) {
char buf[512];
int ret, flags, len;
mbedtls_entropy_context entropy;
mbedtls_ctr_drbg_context ctr_drbg;
mbedtls_ssl_context ssl;
mbedtls_x509_crt cacert;
mbedtls_ssl_config conf;
mbedtls_net_context server_fd;
mbedtls_ssl_init(&ssl);
mbedtls_x509_crt_init(&cacert);
mbedtls_ctr_drbg_init(&ctr_drbg);
ESP_LOGI(TAG, "Seeding the random number generator");
mbedtls_ssl_config_init(&conf);
mbedtls_entropy_init(&entropy);
if((ret = mbedtls_ctr_drbg_seed(&ctr_drbg, mbedtls_entropy_func, &entropy,
NULL, 0)) != 0) {
ESP_LOGE(TAG, "mbedtls_ctr_drbg_seed returned %d", ret);
abort();
}
ESP_LOGI(TAG, "Attaching the certificate bundle...");
ret = esp_crt_bundle_attach(&conf);
if(ret < 0) {
ESP_LOGE(TAG, "esp_crt_bundle_attach returned -0x%x\n\n", -ret);
abort();
}
ESP_LOGI(TAG, "Setting hostname for TLS session...");
/* Hostname set here should match CN in server certificate */
if((ret = mbedtls_ssl_set_hostname(&ssl, WEB_SERVER)) != 0) {
ESP_LOGE(TAG, "mbedtls_ssl_set_hostname returned -0x%x", -ret);
abort();
}
ESP_LOGI(TAG, "Setting up the SSL/TLS structure...");
if((ret = mbedtls_ssl_config_defaults(&conf,
MBEDTLS_SSL_IS_CLIENT,
MBEDTLS_SSL_TRANSPORT_STREAM,
MBEDTLS_SSL_PRESET_DEFAULT)) != 0) {
ESP_LOGE(TAG, "mbedtls_ssl_config_defaults returned %d", ret);
goto exit;
}
/* MBEDTLS_SSL_VERIFY_OPTIONAL is bad for security, in this example it will print
a warning if CA verification fails but it will continue to connect.
You should consider using MBEDTLS_SSL_VERIFY_REQUIRED in your own code.
*/
mbedtls_ssl_conf_authmode(&conf, MBEDTLS_SSL_VERIFY_OPTIONAL);
// root caã®èªã¿è¾¼ã¿ã¨ã‚»ãƒƒã‚·ãƒ§ãƒ³ãƒã‚±ãƒƒãƒˆã‚’有効ã«ã—ã¦ãŠã„ãŸ
// ã‚ã¨ã¯TLSã®éµäº¤æ›ãƒ¢ãƒ¼ãƒ‰ã®è¨å®šã€re-negotiationã¯ã¨ã‚Šã‚ãˆãšç„¡åŠ¹ã«
// TLSã®æœ€å¤§ãƒ»æœ€å°ãƒãƒ¼ã‚¸ãƒ§ãƒ³ã‚’TLS 1.3固定
// 上記ã®è¨˜è¼‰ã®ã¨ãŠã‚Šã€ã‚µãƒ³ãƒ—ルãªã®ã§ã€æœ¬æ¥ã¯ã¡ã‚ƒã‚“ã¨VERIFYã™ã‚‹ã“ã¨!!
mbedtls_x509_crt_parse( &cacert, gtsr1_pem, sizeof(gtsr1_pem) );
mbedtls_ssl_conf_session_tickets( &conf, MBEDTLS_SSL_SESSION_TICKETS_ENABLED );
mbedtls_ssl_conf_tls13_key_exchange_modes( &conf, MBEDTLS_SSL_TLS1_3_KEY_EXCHANGE_MODE_ALL );
mbedtls_ssl_conf_renegotiation( &conf, MBEDTLS_SSL_RENEGOTIATION_DISABLED );
mbedtls_ssl_conf_min_version( &conf, MBEDTLS_SSL_MAJOR_VERSION_3, MBEDTLS_SSL_MINOR_VERSION_4 );
mbedtls_ssl_conf_max_version( &conf, MBEDTLS_SSL_MAJOR_VERSION_3, MBEDTLS_SSL_MINOR_VERSION_4 );
mbedtls_ssl_conf_ca_chain(&conf, &cacert, NULL);
mbedtls_ssl_conf_rng(&conf, mbedtls_ctr_drbg_random, &ctr_drbg);
#ifdef CONFIG_MBEDTLS_DEBUG
mbedtls_esp_enable_debug_log(&conf, CONFIG_MBEDTLS_DEBUG_LEVEL);
#endif
if ((ret = mbedtls_ssl_setup(&ssl, &conf)) != 0) {
ESP_LOGE(TAG, "mbedtls_ssl_setup returned -0x%x\n\n", -ret);
goto exit;
}
while(1) {
mbedtls_net_init(&server_fd);
ESP_LOGI(TAG, "Connecting to %s:%s...", WEB_SERVER, WEB_PORT);
if ((ret = mbedtls_net_connect(&server_fd, WEB_SERVER,
WEB_PORT, MBEDTLS_NET_PROTO_TCP)) != 0) {
ESP_LOGE(TAG, "mbedtls_net_connect returned -%x", -ret);
goto exit;
}
ESP_LOGI(TAG, "Connected.");
mbedtls_ssl_set_bio(&ssl, &server_fd, mbedtls_net_send, mbedtls_net_recv, NULL);
ESP_LOGI(TAG, "Performing the SSL/TLS handshake...");
while ((ret = mbedtls_ssl_handshake(&ssl)) != 0) {
if (ret != MBEDTLS_ERR_SSL_WANT_READ && ret != MBEDTLS_ERR_SSL_WANT_WRITE) {
ESP_LOGE(TAG, "mbedtls_ssl_handshake returned -0x%x", -ret);
goto exit;
}
}
ESP_LOGI(TAG, "Verifying peer X.509 certificate...");
if ((flags = mbedtls_ssl_get_verify_result(&ssl)) != 0) {
/* In real life, we probably want to close connection if ret != 0 */
ESP_LOGW(TAG, "Failed to verify peer certificate!");
bzero(buf, sizeof(buf));
mbedtls_x509_crt_verify_info(buf, sizeof(buf), " ! ", flags);
ESP_LOGW(TAG, "verification info: %s", buf);
} else {
ESP_LOGI(TAG, "Certificate verified.");
}
ESP_LOGI(TAG, "Cipher suite is %s", mbedtls_ssl_get_ciphersuite(&ssl));
ESP_LOGI(TAG, "Writing HTTP request...");
size_t written_bytes = 0;
do {
ret = mbedtls_ssl_write(&ssl,
(const unsigned char *)REQUEST + written_bytes,
strlen(REQUEST) - written_bytes);
if (ret >= 0) {
ESP_LOGI(TAG, "%d bytes written", ret);
written_bytes += ret;
} else if (ret != MBEDTLS_ERR_SSL_WANT_WRITE && ret != MBEDTLS_ERR_SSL_WANT_READ) {
ESP_LOGE(TAG, "mbedtls_ssl_write returned -0x%x", -ret);
goto exit;
}
} while(written_bytes < strlen(REQUEST));
ESP_LOGI(TAG, "Reading HTTP response...");
do {
len = sizeof(buf) - 1;
bzero(buf, sizeof(buf));
ret = mbedtls_ssl_read(&ssl, (unsigned char *)buf, len);
if(ret == MBEDTLS_ERR_SSL_WANT_READ || ret == MBEDTLS_ERR_SSL_WANT_WRITE)
continue;
if(ret == MBEDTLS_ERR_SSL_PEER_CLOSE_NOTIFY) {
ret = 0;
break;
}
if(ret < 0) {
ESP_LOGE(TAG, "mbedtls_ssl_read returned -0x%x", -ret);
break;
}
if(ret == 0) {
ESP_LOGI(TAG, "connection closed");
break;
}
len = ret;
ESP_LOGD(TAG, "%d bytes read", len);
/* Print response directly to stdout as it is read */
for(int i = 0; i < len; i++) {
putchar(buf[i]);
}
} while(1);
mbedtls_ssl_close_notify(&ssl);
exit:
mbedtls_ssl_session_reset(&ssl);
mbedtls_net_free(&server_fd);
if(ret != 0) {
mbedtls_strerror(ret, buf, 100);
ESP_LOGE(TAG, "Last error was: -0x%x - %s", -ret, buf);
}
putchar('\n'); // JSON output doesn't have a newline at end
static int request_count;
ESP_LOGI(TAG, "Completed %d requests", ++request_count);
printf("Minimum free heap size: %d bytes\n", esp_get_minimum_free_heap_size());
for(int countdown = 10; countdown >= 0; countdown--) {
ESP_LOGI(TAG, "%d...", countdown);
vTaskDelay(1000 / portTICK_PERIOD_MS);
}
ESP_LOGI(TAG, "Starting again!");
}
}
void app_main(void) {
ESP_ERROR_CHECK( nvs_flash_init() );
ESP_ERROR_CHECK(esp_netif_init());
ESP_ERROR_CHECK(esp_event_loop_create_default());
/* This helper function configures Wi-Fi or Ethernet, as selected in menuconfig.
* Read "Establishing Wi-Fi or Ethernet Connection" section in
* examples/protocols/README.md for more information about this function.
*/
ESP_ERROR_CHECK(example_connect());
xTaskCreate(&https_get_task, "https_get_task", 8192, NULL, 5, NULL);
}ã‚ã¨ã¯ESP32ã«ãƒ•ãƒ©ãƒƒã‚·ãƒ¥ã—ã¦å®Ÿéš›ã«ã‚·ãƒªã‚¢ãƒ«çµŒç”±ã§æ›¸ã込んã§ã€å®Ÿéš›ã«TLS 1.3㧠www.google.com ã«ã‚¢ã‚¯ã‚»ã‚¹ã§ãã‚‹ã“ã¨ã‚’確èªã—ã¾ã™ã€‚
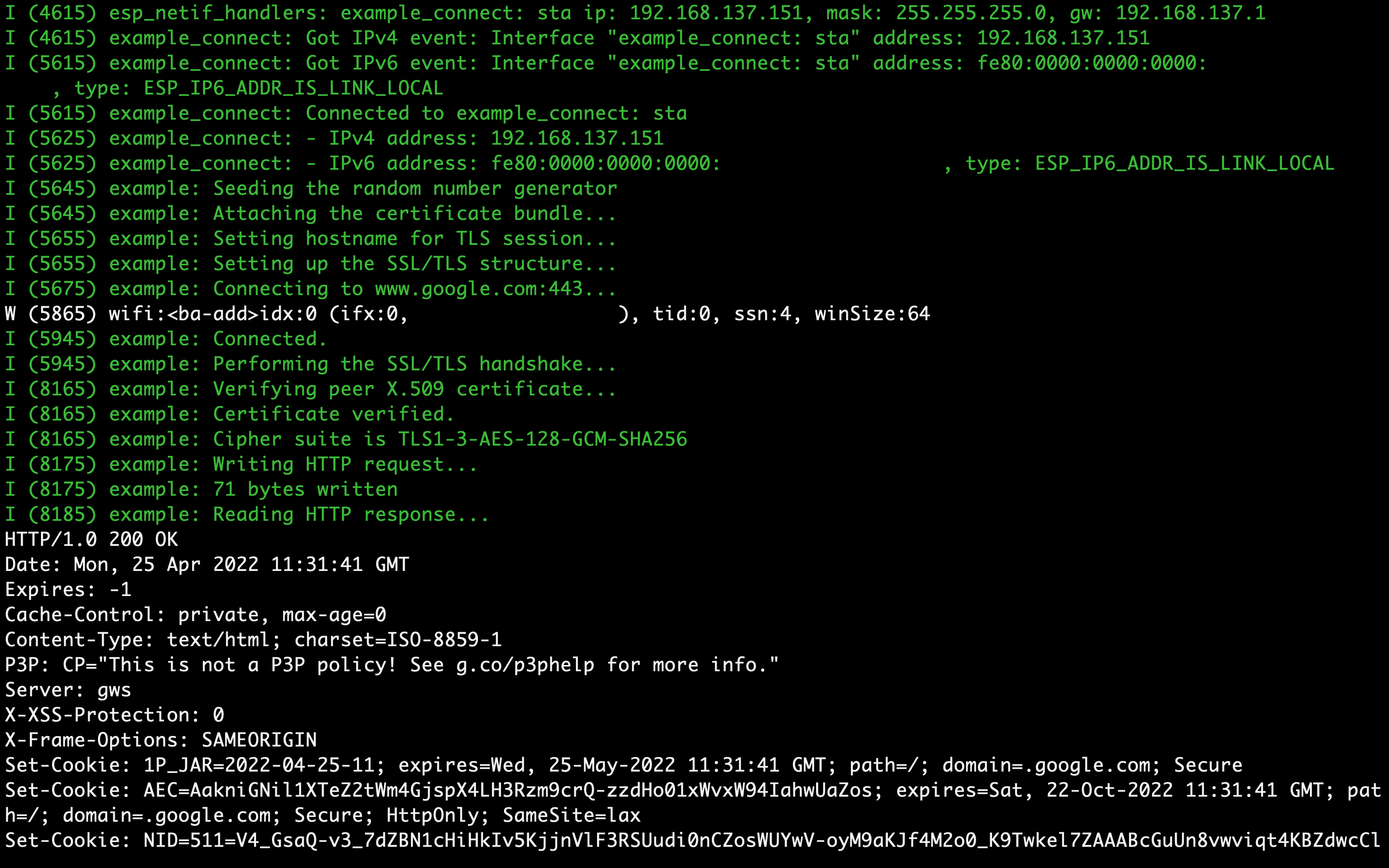
ã©ã†ã‚„らãƒãƒƒãƒãƒªã‚¢ã‚¯ã‚»ã‚¹ã§ãã¦ã„るよã†ã§ã™ã€‚ã“ã®æ™‚ã¯Windows PCã®ãƒ¢ãƒã‚¤ãƒ«ãƒ›ãƒƒãƒˆã‚¹ãƒãƒƒãƒˆã‚’利用ã—ã¦ã€Wiresharkã§ãƒ‘ケットã‚ャプãƒãƒ£ãƒ¼ã‚’ã—ã¾ã—ãŸãŒã€ã“ã¡ã‚‰ã‚‚TLS 1.3ã§ã‚¢ã‚¯ã‚»ã‚¹ã—ã¦ã„ã‚‹ãƒã‚°ãŒå–ã‚Œã¾ã—ãŸã€‚
QUICã®æš—å·åŒ–ã‚’è¡Œã†
ã“ã“ã¾ã§ã‚„ã£ãŸã‚‰ã€mbedTLS を使ã£ã¦QUICã®æš—å·åŒ–・復å·åŒ–ã‚’ã—ãŸããªã‚‹ã®ã¯äººã®æ€§ã§ã™ã。ã“ã“ã§ã¯ã€RFC 9001ã®Appendix Aã«ã‚るサンプルパケットを使ã£ã¦ã‚„ã£ã¦ã¿ã¾ã™ã€‚
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include "common.h"
#include "mbedtls/platform.h"
#include "mbedtls/net_sockets.h"
#include "mbedtls/ssl.h"
#include "mbedtls/entropy.h"
#include "mbedtls/ctr_drbg.h"
#include "mbedtls/hmac_drbg.h"
#include "mbedtls/x509.h"
#include "mbedtls/error.h"
#include "mbedtls/debug.h"
#include "mbedtls/timing.h"
#include "mbedtls/base64.h"
#include "mbedtls/hkdf.h"
#include "mbedtls/gcm.h"
#include <ssl_misc.h>
#include "ssl_tls13_keys.h"
#define BUFFER_SIZE 2000
// RFC 9001, 5.2. Initial Secrets, salt
unsigned char salt[20] = {
0x38,0x76,0x2c,0xf7,0xf5,0x59,0x34,0xb3,0x4d,0x17,0x9a,0xe6,0xa4,0xc8,0x0c,0xad,
0xcc,0xbb,0x7f,0x0a};
// RFC 9001, Appendix A.2. Client Initial QUIC long header
// c300000001088394c8f03e5157080000449e00000002
// c3 = long header(1byte)
// 00 00 00 01 = version (4byte)
// 08 = DCID Len (1byte)
// 83 94 c8 f0 3e 51 57 08 = Destination Connection ID (8byte)
// 00 = SCID Len(1byte)
// 00 = Token Length (1byte)
// 449e = length = 1182 (2byte)
// 00 00 00 02 = packet number = 2(pn_length)
unsigned char plane_header[22] = {
0xc3,0x00,0x00,0x00,0x01,0x08,0x83,0x94,0xc8,0xf0,0x3e,0x51,0x57,0x08,0x00,0x00,
0x44,0x9e,0x00,0x00,0x00,0x02};
// RFC 9001, Appendix A.2. Client Initial payload
unsigned char plane_payload[245] = {
0x06,0x00,0x40,0xf1,0x01,0x00,0x00,0xed,0x03,0x03,0xeb,0xf8,0xfa,0x56,0xf1,0x29,
0x39,0xb9,0x58,0x4a,0x38,0x96,0x47,0x2e,0xc4,0x0b,0xb8,0x63,0xcf,0xd3,0xe8,0x68,
0x04,0xfe,0x3a,0x47,0xf0,0x6a,0x2b,0x69,0x48,0x4c,0x00,0x00,0x04,0x13,0x01,0x13,
0x02,0x01,0x00,0x00,0xc0,0x00,0x00,0x00,0x10,0x00,0x0e,0x00,0x00,0x0b,0x65,0x78,
0x61,0x6d,0x70,0x6c,0x65,0x2e,0x63,0x6f,0x6d,0xff,0x01,0x00,0x01,0x00,0x00,0x0a,
0x00,0x08,0x00,0x06,0x00,0x1d,0x00,0x17,0x00,0x18,0x00,0x10,0x00,0x07,0x00,0x05,
0x04,0x61,0x6c,0x70,0x6e,0x00,0x05,0x00,0x05,0x01,0x00,0x00,0x00,0x00,0x00,0x33,
0x00,0x26,0x00,0x24,0x00,0x1d,0x00,0x20,0x93,0x70,0xb2,0xc9,0xca,0xa4,0x7f,0xba,
0xba,0xf4,0x55,0x9f,0xed,0xba,0x75,0x3d,0xe1,0x71,0xfa,0x71,0xf5,0x0f,0x1c,0xe1,
0x5d,0x43,0xe9,0x94,0xec,0x74,0xd7,0x48,0x00,0x2b,0x00,0x03,0x02,0x03,0x04,0x00,
0x0d,0x00,0x10,0x00,0x0e,0x04,0x03,0x05,0x03,0x06,0x03,0x02,0x03,0x08,0x04,0x08,
0x05,0x08,0x06,0x00,0x2d,0x00,0x02,0x01,0x01,0x00,0x1c,0x00,0x02,0x40,0x01,0x00,
0x39,0x00,0x32,0x04,0x08,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0xff,0x05,0x04,0x80,
0x00,0xff,0xff,0x07,0x04,0x80,0x00,0xff,0xff,0x08,0x01,0x10,0x01,0x04,0x80,0x00,
0x75,0x30,0x09,0x01,0x10,0x0f,0x08,0x83,0x94,0xc8,0xf0,0x3e,0x51,0x57,0x08,0x06,
0x04,0x80,0x00,0xff,0xff};
// 16進ダンプ用
void keydump(unsigned char *key, int length) {
for (int i = 0; i < length; i++) {
if (i != 0 && i % 32 == 0) printf("\n");
else if (i != 0 && i % 16 == 0) printf(" ");
printf ("%02x", key[i]);
}
printf("\n");
}
// mbedTLSを使ã£ã¦AES128_GCM æš—å·åŒ–(ã¨ã‚Šã‚ãˆãšã‚µãƒ³ãƒ—ルãªã®ã§retã¯ã‚¹ãƒ«ãƒ¼)
int encrypt_payload(unsigned char *key, size_t keylen,
unsigned char *iv, size_t ivsize,
unsigned char *ad, size_t adsize,
unsigned char *from, size_t fromsize,
unsigned char *to, size_t tosize, size_t *olen) {
int ret;
mbedtls_gcm_context ctx;
mbedtls_cipher_id_t cipher = MBEDTLS_CIPHER_ID_AES;
int output_len;
unsigned char tag_output[16];
size_t tag_len = sizeof(tag_output);
size_t tmpolen;
// éµãƒ»Associated Dataã€é›»æ–‡ã‚’è¨å®šã—ã¦æš—å·åŒ–
mbedtls_gcm_init(&ctx);
ret = mbedtls_gcm_setkey(&ctx, cipher, key, keylen);
// mbedtls_gcm_crypt_and_tag ã¨åŒç‰ã®å‡¦ç†
ret = mbedtls_gcm_starts(&ctx, MBEDTLS_GCM_ENCRYPT, iv, ivsize);
ret = mbedtls_gcm_update_ad(&ctx, ad, adsize);
ret = mbedtls_gcm_update(&ctx, from, fromsize, to, tosize, olen);
ret = mbedtls_gcm_finish(&ctx, NULL, 0, &tmpolen, tag_output, sizeof(tag_output) );
// 最後ã«tagを付与ã™ã‚‹
memcpy(to + *olen, tag_output, sizeof(tag_output));
*olen = *olen + 16;
mbedtls_gcm_free(&ctx);
return ret;
}
int main() {
int ret = 0;
unsigned char enc_payload[BUFFER_SIZE + 1];
// デãƒãƒƒã‚°ãƒ¬ãƒ™ãƒ«ã‚’3ã«ã—ã¦ãŠã
mbedtls_debug_set_threshold( 3 );
// client secret/key/iv/hp ã‚’ salt, did(distinatin connection id) ã‹ã‚‰å–å¾—
const mbedtls_md_info_t *md = mbedtls_md_info_from_type( MBEDTLS_MD_SHA256 );
unsigned char initial_secret[mbedtls_md_get_size(md)];
ret = mbedtls_hkdf_extract( md, salt, 20, plane_header+6, 8, &initial_secret);
unsigned char client_secret[32];
unsigned char client_key[16];
unsigned char client_iv[12];
unsigned char client_hp[16];
mbedtls_ssl_tls13_hkdf_expand_label(MBEDTLS_MD_SHA256, initial_secret, 32, "client in", 9, NULL, 0, &client_secret, 32);
mbedtls_ssl_tls13_hkdf_expand_label(MBEDTLS_MD_SHA256, client_secret, 32, "quic key", 8, NULL, 0, &client_key, 16);
mbedtls_ssl_tls13_hkdf_expand_label(MBEDTLS_MD_SHA256, client_secret, 32, "quic iv", 7, NULL, 0, &client_iv, 12);
mbedtls_ssl_tls13_hkdf_expand_label(MBEDTLS_MD_SHA256, client_secret, 32, "quic hp", 7, NULL, 0, &client_hp, 16);
keydump(initial_secret, mbedtls_md_get_size(md));
keydump(client_secret, 32);
keydump(client_key, 16);
keydump(client_iv, 12);
keydump(client_hp, 16);
// æš—å·åŒ–ã™ã‚‹ãƒšã‚¤ãƒãƒ¼ãƒ‰ã®æº–備をã™ã‚‹
int padding = 1200 // QUIC UDP initialize packet size
- 1 // Flags
- 4 // version
- 1 // Destination Connectin ID length
- 8 // Destination Connectin ID
- 1 // Source Connection ID length
- 0 // Source Connection ID
- 1 // Token Length
- 2 // length len
- ((plane_header[0] & 0x03) + 1) // packet number length
- sizeof(plane_payload)
- 16;
uint32_t packet_number = *(plane_header + 18) << 24
| *(plane_header + 19) << 16
| *(plane_header + 20) << 8
| *(plane_header + 21) << 0;
unsigned char payload[padding + sizeof(plane_payload)];
// 実際ã«é€ä¿¡ã™ã‚‹ãƒ‡ãƒ¼ã‚¿ã‹ã‚‰0パディングã™ã‚‹
memset(payload, 0, sizeof(payload));
memcpy(payload, plane_payload, sizeof(plane_payload));
// æš—å·åŒ–ã™ã‚‹ãŸã‚ã®nonceを用æ„ã™ã‚‹ RFC9001 5.3. AEAD Usage
unsigned char nonce[12];
unsigned int olen;
memcpy(nonce, client_iv, sizeof(client_iv));
nonce[11] = nonce[11] ^ packet_number;
keydump(nonce, 12);
// ペイãƒãƒ¼ãƒ‰ã®æš—å·åŒ–実行
encrypt_payload(client_key, sizeof(client_key)*8,
nonce, sizeof(nonce),
plane_header, sizeof(plane_header),
payload, sizeof(payload),
enc_payload, sizeof(enc_payload), &olen);
keydump(enc_payload, olen);
// QUICヘッダã®ä¿è·ã®ãŸã‚ã®ãƒžã‚¹ã‚¯ã‚’ç”¨æ„ RFC9001 5.4.2. Header Protection Sample
// sample_offset : 22(payloadã®å…ˆé 16byte)
mbedtls_aes_context aes;
unsigned char header_mask[16];
mbedtls_aes_init(&aes);
mbedtls_aes_setkey_enc( &aes, (const unsigned char*) client_hp, sizeof(client_hp) * 8 );
mbedtls_aes_crypt_ecb( &aes, MBEDTLS_AES_ENCRYPT, (const unsigned char*)enc_payload, header_mask);
mbedtls_aes_free( &aes );
keydump(header_mask, 16);
// ヘッダã«ãƒžã‚¹ã‚¯
plane_header[0] ^= header_mask[0] & 0x0f;
for (int i = 0; i < 4; i++)
plane_header[18 + i] ^= header_mask[1 + i];
keydump(plane_header, sizeof(plane_header));
// [ä¿è·ã•ã‚ŒãŸãƒ˜ãƒƒãƒ€ + æš—å·åŒ–ã•ã‚ŒãŸãƒšã‚¤ãƒãƒ¼ãƒ‰] ã«ã—ã¦ãƒ€ãƒ³ãƒ—
unsigned char encpacket[olen + sizeof(plane_header)];
memcpy(encpacket, plane_header, sizeof(plane_header));
memcpy(encpacket + sizeof(plane_header), enc_payload, olen);
keydump(encpacket, olen + sizeof(plane_header));
return 0;
}ã“れ㧔ä¿è·ã•ã‚ŒãŸãƒ˜ãƒƒãƒ€+æš—å·åŒ–ã•ã‚ŒãŸãƒšã‚¤ãƒãƒ¼ãƒ‰”ã®ä¿è·ã•ã‚ŒãŸãƒ‘ケットãŒï¼ˆenc_payload)〔c000000001088 …. 018ab0856972e194cd934″ ã¨A.2. Client Initialã®çµæžœã¨åˆè‡´ã—ã¦ã„ã‚‹ã¯ãšã§ã™ã€‚復å·åŒ–ã¯ã“ã®é€†ã‚’ã‚„ã‚Œã°OKã¨ã„ã£ãŸæ„Ÿã˜ã§ã™ã€‚ã“ã®æš—å·åŒ–・復å·åŒ–ã‚‚esp-idf(ESP32)ã§ã®å‹•ä½œç¢ºèªã‚‚出æ¥ã¾ã—ãŸã€‚
実際ã«ãƒ—ãƒãƒˆã‚³ãƒ«ã‚’ç†è§£ã™ã‚‹ã«ã¯ã€å…ˆé”ã®å®Ÿè£…やサンプルをå‚考ã«ã—ãŸã‚Šã€RFCã‚’èªã¿ãªãŒã‚‰ã‚µãƒ³ãƒ—ルコードを書ã„ã¦å‹•ã‹ã—ã¦ã€Wiresharkã§ãƒ‘ケットを観察ã—㦅ã¨ã„ã†åœ°é“ãªæ–¹æ³•ãŒè‰¯ã„ã‹ãªã¨æ€ã£ã¦ã„ãŸã‚Šã—ã¾ã™ã€‚æš—å·åŒ–・復å·åŒ–ã‚’mbedTLSを使ã£ã¦å‡ºæ¥ãã†ãªã®ã§ã€æ¬¡ã¯çµ„è¾¼ã¿ç«¯æœ«ä¸Šã§QUICã§é€šä¿¡ã‚’è¡Œã†æ‰€ã¾ã§ã‚„ã£ã¦ã¿ã‚ˆã†ã‹ãªã¨ã€‚
ãŸã ã—ã€ã‚ˆã僕ãŒåˆ©ç”¨ã™ã‚‹ç«¯æœ«ã ã¨æ™‚刻をæŒã£ã¦ã„ãªã‹ã£ãŸã‚Šï¼ˆgettimeç³»ãªã©ã¯è‡ªä½œã™ã‚‹ï¼‰ã€é€šä¿¡ç³»ã®ã‚¤ãƒ³ã‚¿ãƒ•ã‚§ã‚¤ã‚¹ãŒç‹¬è‡ªã ã£ãŸã‚Šï¼ˆlwipã¯ã‚ˆã見ã¾ã™ãŒï¼‰ã€åˆ©ç”¨ã™ã‚‹çµ„è¾¼ã¿ç’°å¢ƒã«ã†ã¾ãåˆã‚ã›ã¦…ã¨ã„ã£ãŸæ„Ÿã˜ã«ãªã£ã¦ãã¾ã™ã。
ブãƒã‚°ã®è‘—者欄
æŽ¡ç”¨æƒ…å ±
関連記事
KEYWORD
CATEGORY
-
æŠ€è¡“æƒ…å ±ï¼ˆ562)
- フレームワーク(4)
- モãƒã‚¤ãƒ«ï¼ˆ2)
- ミドルウェア(1)
- ãƒãƒœãƒƒãƒˆï¼ˆ8)
- 3DCG(2)
- インフラ(148)
- クラウド(21)
- ã‚»ã‚ュリティ(56)
- ãƒãƒƒãƒˆãƒ¯ãƒ¼ã‚¯ï¼ˆ26)
- フãƒãƒ³ãƒˆã‚¨ãƒ³ãƒ‰ï¼ˆ23)
- ãƒãƒƒã‚¯ã‚¨ãƒ³ãƒ‰ï¼ˆ21)
- AI/機械å¦ç¿’(102)
- æ¥å‹™åŠ¹çŽ‡åŒ–(81)
- マãƒã‚¸ãƒ¡ãƒ³ãƒˆï¼ˆ21)
- developer(23)
- 登壇レãƒãƒ¼ãƒˆï¼ˆ96)
-
イベント(209)
-
カルãƒãƒ£ãƒ¼ï¼ˆ54)
-
デザイン(54)
-
インターンシップ(2)
TAG
- "eVTOL"
- "Japan Drone"
- "ãƒãƒœãƒ†ã‚£ã‚¯ã‚¹"
- "空飛ã¶ã‚¯ãƒ«ãƒž"
- 5G
- Adam byGMO
- AdventCalender
- AGI
- AI
- AI 機械å¦ç¿’強化å¦ç¿’
- AIエージェント
- AI人財
- AMD
- APT攻撃
- AWX
- BIT VALLEY
- Blade
- blockchain
- Canva
- ChatGPT
- ChatGPT Team
- Claude Team
- cloudflare
- cloudnative
- CloudStack
- CM
- CNDO
- CNDT
- CODEBLUE
- CODEGYM Academy
- ConoHa
- ConoHaã€Dify
- CS
- CSS
- CTF
- DC
- design
- Designship
- Desiner
- DeveloperExper
- DeveloperExpert
- DevRel
- DevSecOpsThon
- DiceCTF
- Dify
- DNS
- Docker
- DTF
- Excel
- Expert
- Experts
- Felo
- GitLab
- GMO AIR
- GMO AIãƒãƒœãƒ†ã‚£ã‚¯ã‚¹å¤§ä¼šè°ï¼†è¡¨å½°å¼
- GMO DESIGN AWARD
- GMO Developers Day
- GMO Developers Night
- GMO Developers ブãƒã‚°
- GMO Flatt Security
- GMO GPUクラウド
- GMO Hacking Night
- GMO kitaQ
- GMO SONIC
- GMOアドパートナーズ
- GMOアドマーケティング
- GMOイエラエ
- GMOインターãƒãƒƒãƒˆ
- GMOインターãƒãƒƒãƒˆã‚°ãƒ«ãƒ¼ãƒ—
- GMOクラウド]
- GMOã‚°ãƒãƒ¼ãƒãƒ«ã‚µã‚¤ãƒ³
- GMOコãƒã‚¯ãƒˆ
- GMOサイãƒãƒ¼ã‚»ã‚ュリティbyイエラエ
- GMOサイãƒãƒ¼ã‚»ã‚ュリティ大会è°
- GMOサイãƒãƒ¼ã‚»ã‚ュリティ大会è°ï¼†è¡¨å½°å¼
- GMOソリューションパートナー
- GMOデジã‚ッズ
- GMOブランドセã‚ュリティ
- GMOペイメントゲートウェイ
- GMOペパボ
- GMOメディア
- GMOリサーãƒ
- GMO大会è°
- Go
- GPU
- GPUクラウド
- GTB
- Hardning
- Harvester
- HCI
- INCYBER Forum
- iOS
- IoT
- ISUCON
- JapanDrone
- Java
- JJUG
- K8s
- Kaigi on Rails
- Kids VALLEY
- KidsVALLEY
- Linux
- LLM
- MCP
- MetaMask
- MySQL
- NFT
- NVIDIA
- NW構æˆå›³
- NWè¨å®š
- Ollama
- OpenStack
- Perl
- perplexity
- PHP
- PHPcon
- PHPerKaigi
- PHPカンファレンス
- Python
- QUIC
- Rancher
- RPA
- Ruby
- Selenium
- Slack
- Slack活用
- Spectrum Tokyo Meetup
- splunk
- SRE
- sshd
- SSL
- Terraform
- TLS
- TypeScript
- UI/UX
- vibe
- VLAN
- VS Code
- Webアプリケーション
- WEBディレクター
- XSS
- アドベントカレンダー
- イベントレãƒãƒ¼ãƒˆ
- インターンシップ
- インãƒã‚¦ã‚¹
- オブジェクト指å‘
- オンボーディング
- ãŠåå‰.com
- カルãƒãƒ£ãƒ¼
- クリエイター
- クリエイティブ
- コーディング
- コンテナ
- サイãƒãƒ¼ã‚»ã‚ュリティ
- サマーインターン
- ã‚·ã‚¹ãƒ†ãƒ ç ”ä¿®
- スクラãƒ
- スペシャリスト
- ã‚»ã‚ュリティ
- ソフトウェアテスト
- ãƒãƒ¼ãƒ ビルディング
- デザイナー
- デザイン
- テスト
- ドãƒãƒ¼ãƒ³
- ãƒãƒƒãƒˆã®ã‚»ã‚ュリティもGMO
- ãƒãƒƒãƒˆãƒ¯ãƒ¼ã‚¯
- ビジãƒã‚¹è·
- ヒューマノイド
- ヒューマノイドãƒãƒœãƒƒãƒˆ
- フィジカルAI
- プãƒã‚°ãƒ©ãƒŸãƒ³ã‚°æ•™è‚²
- ブãƒãƒƒã‚¯ãƒã‚§ãƒ¼ãƒ³
- ベイズ統計å¦
- マイクãƒã‚µãƒ¼ãƒ“ス
- マルãƒãƒ—レイ
- ミドルウェア
- モãƒã‚¤ãƒ«
- ゆã‚ã¿ã‚‰ã„ワーク
- リモートワーク
- レンタルサーãƒãƒ¼
- ãƒãƒœãƒƒãƒˆ
- 京大ミートアップ
- 人ææ´¾é£
- 出展レãƒãƒ¼ãƒˆ
- å‹•ç”»
- å”賛レãƒãƒ¼ãƒˆ
- 基礎
- å¤šæ‹ ç‚¹é–‹ç™º
- 大å¦æŽˆæ¥
- 宮崎オフィス
- 展示会
- 広告
- 強化å¦ç¿’
- å½¢
- 応用
- æƒ…å ±ä¼é”
- 技育プãƒã‚¸ã‚§ã‚¯ãƒˆ
- æŠ€è¡“åºƒå ±
- 技術書典
- 採用
- 採用サイトリニューアル
- 採用活動
- æ–°å’
- æ–°å’ç ”ä¿®
- 日本科å¦æœªæ¥é¤¨
- æ˜ åƒ
- æ˜ åƒã‚¯ãƒªã‚¨ã‚¤ã‚¿ãƒ¼
- æš—å·
- æ¥å‹™åŠ¹çŽ‡åŒ–
- æ¥å‹™æ™‚間削減
- 機械å¦ç¿’
- 決済
- 物ç†æš—å·
- 生æˆAI
- 色
- 視覚暗å·
- 開発生産性
- 開発生産性å‘上
- 階層ベイズ
- 高機能暗å·
PICKUP
-

属人化×ガラパゴス化ã‹ã‚‰ã®è„±å´ï¼šèª²é‡‘基盤改善プãƒã‚¸ã‚§ã‚¯ãƒˆã®èˆžå°è£
æŠ€è¡“æƒ…å ±
-

ConoHa VPSã§ä½œã‚‹ BungeeCord+複数Minecraftサーãƒæ§‹æˆå…¥é–€
æŠ€è¡“æƒ…å ±
-

VPS基盤ã«ãŠã‘ã‚‹CPUé¸å®šã®æ€è€ƒãƒ—ãƒã‚»ã‚¹
æŠ€è¡“æƒ…å ±
-

「インãƒã‚¦ã‚¹å‹•ç”»ã‚µãƒŸãƒƒãƒˆ2026ã€é–‹å‚¬æ±ºå®šï¼
イベント
-

「エンジニアã®æˆé•·ãŒã‚¹ãƒˆãƒƒãƒ—ã™ã‚‹ç†ç”±ã¨ãã®å¯¾ç–ã€
æŠ€è¡“æƒ…å ±
-

フィジカルAI × ãƒãƒœãƒ†ã‚£ã‚¯ã‚¹ã®ç™¾å®¶äº‰é³´ – CES 2026ç¾åœ°å ±å‘Šãƒ¬ãƒãƒ¼ãƒˆ
æŠ€è¡“æƒ…å ±









